Blockchain Weakness Classification (BWC)
A taxonomy for classifying smart contract vulnerabilities.
Last Update: Feb 2 2026
Authors: @BBHGuild
BWC Top 11
| Blockchain Weakness Classification | Description | Exploit Methods | Mitigation | ||
|---|---|---|---|---|---|
BWC 1: Ecosystem & Off-Chain Risks | BWC 1.1: Foundational Design Flaws (Trustlessness) | BWC 1.1.1: Indispensable Intermediaries | The system violates the "No Indispensable Intermediaries" law. It relies on specific actors (sequencers, relayers, provers, admin keys) that cannot be replaced by an ordinary participant. If these actors misbehave or disappear, the system halts or censors. | ||
BWC 1.1.2: Barriers to Verification (The Specialist Gap) | The system is theoretically open but practically closed due to excessive complexity or resource requirements. This violates the "Accessibility" principle, creating a class system where verification is a privilege for specialists, forcing users to "trust the dashboard." | ||||
BWC 1.1.3: Reliance on Critical Secrets | The system violates the "No Critical Secrets" law. It relies on private information (mempools, off-chain order books, server-side keys) held by a single actor to function or determine state transitions. | ||||
BWC 1.1.4: Forced Delegation (Loss of Sovereignty) | The system replaces Delegation (optional convenience) with Dependence (mandatory reliance). Users cannot interact with the protocol directly but must route through a specific UI, API, or relayer that acts as a landlord. | ||||
BWC 1.1.5: Lack of Credible Neutrality | The base layer discriminates against specific users or use cases. Instead of "math and consensus," the protocol enforces policy, becoming a "Platform" rather than a neutral "Protocol." | ||||
BWC 1.1.6: Unverifiable Outcomes | The system violates the "No Unverifiable Outcomes" law. Effects on the state cannot be strictly reproduced from public data, requiring "Blind Trust" in an oracle or multisig. | ||||
BWC 1.1.7: User Disempowerment & Extractive Design ("Corposlop") | The system prioritizes corporate metrics (market cap, engagement) over user sovereignty. It uses "corporate optimization power" and a "respectable aura" to mask behavior that extracts value from users rather than empowering them. This manifests in four key ways: 1. Attention & Dopamine Extraction: Hijacking attention for short-term engagement (addiction). 2. Surveillance & Data Commodification: Needless data collection to create sellable assets. 3. Walled Gardens: Preventing exit or interoperability (Monopolistic Lock-in). 4. Predatory Financialization: Marketing high-risk gambling as "investing" (Gamblification). | ||||
BWC 1.2: Identity & Key Management Failures | BWC 1.2.1: Compromised Device/OS | Vulnerabilities in user devices or operating systems leading to private key theft, session hijacking, or malicious transaction approvals. | |||
BWC 1.2.2: Private Key Leakage | Accidental or intentional exposure of private keys, granting unauthorized access to funds. | ||||
BWC 1.2.3: Insider Threat | Current or former employees, contractors, or partners intentionally misusing their authorized access to compromise a system. | ||||
BWC 1.2.4: Wrench Attacks | An attacker uses physical violence, coercion, or threats (shifting toward psychological warfare and AI-enhanced tactics) to force a victim to surrender their private keys or assets, bypassing all technical security measures. | Threat Evolution: | |||
BWC 1.2.5: Vulnerable Vanity/Address Generators | Flaws in tools used to create custom, human-readable addresses (e.g., starting with 0xdead...) that result in predictable or non-random private keys. | ||||
BWC 1.3: Social Engineering & Deception | BWC 1.3.1: Social Engineering Exploits | Tricking users into revealing sensitive information or performing actions against their interest through deception. Many modern campaigns are executed via "Drainer-as-a-Service" platforms, where affiliates use sophisticated kits to target users. | |||
BWC 1.3.2: SIM Swap Attack | An attacker illegally obtains a new SIM card for a victim's phone number, allowing them to intercept 2FA codes sent via SMS. | ||||
BWC 1.3.3: Front-End Hijack/Spoofing | Modifying a DApp's web interface to trick users into approving malicious transactions or revealing secrets. Attackers often use advanced "cloaking" to hide malicious payloads from security researchers while presenting them to targeted victims. | ||||
BWC 1.3.4: Fake Wallet Applications | Malicious mobile or desktop apps that impersonate legitimate wallets to steal private keys or seed phrases. | ||||
BWC 1.3.5: Malicious Browser Extensions | Browser extensions that steal secrets or inject malicious scripts into DApp front-ends. | ||||
BWC 1.3.6: Malicious RPC Provider | A custom RPC endpoint that returns false data to trick a user or wallet into signing a malicious transaction. | ||||
BWC 1.3.7: Flawed Off-Chain Infrastructure | Design flaws in critical off-chain components (e.g., keeper bots, oracle nodes) that are essential for protocol health, causing them to fail under stressful or unexpected conditions like high network congestion. | ||||
BWC 1.3.8: Sybil Attacks | A single entity creates a large number of pseudonymous identities to gain a disproportionate advantage in a system. This undermines mechanisms that assume unique participants, such as airdrop distributions, governance voting, and reputation systems. | ||||
BWC 1.4: Infrastructure & Supply Chain Integrity | BWC 1.4.1: Compromised Validator/Node | A validator or node operator is compromised, leading to malicious activities like transaction censorship, reordering, or double-spending. | |||
BWC 1.4.2: DNS Hijacking Attacks | Redirecting traffic from a legitimate DApp website to a fraudulent phishing site by compromising DNS servers. | ||||
BWC 1.4.3: Compromised Communication Platforms | Hijacking of official project accounts (Discord, X/Twitter, Telegram) to post phishing links or spread misinformation. | ||||
BWC 1.4.4: Supply Chain Attacks | Compromises in the development pipeline, including malicious dependencies, backdoored developer tools (compilers, IDEs), or insecure deployment processes. | ||||
BWC 1.4.5: Client Consensus Bug | A bug in a client's implementation of a core protocol rule (e.g., state root computation, block validation) that causes it to fail to reach or maintain consensus with the rest of the network. | ||||
BWC 1.4.6: Client API Bug | A bug in a client's RPC/API layer that returns incorrect or misleading data to users or applications, potentially leading to flawed transactions or an incorrect view of on-chain state. | ||||
BWC 1.4.7: Communication Link Hijacking | Failure to maintain ownership of critical communication links (e.g., social media vanity URLs), allowing scammers to claim the expired links and impersonate the project. This turns all historical references to that link into phishing traps. | ||||
BWC 1.5: Nation-State & Advanced Persistent Threats (APTs) | BWC 1.5.1: Coordinated Multi-Vector Attacks | Sophisticated, large-scale attacks, often attributed to nation-states or organized crime (e.g., Lazarus Group), that combine multiple tactics simultaneously. | |||
BWC 1.5.2: State-Sponsored Infrastructure Compromise | Nation-state actors targeting core internet infrastructure (e.g., DNS, BGP, certificate authorities) to intercept or redirect traffic for entire ecosystems. | ||||
BWC 1.5.3: Geopolitical Economic Warfare | Using blockchain and DeFi protocols as instruments of economic warfare, such as evading sanctions or destabilizing the financial systems of rival states. | ||||
BWC 1.5.4: Cross-Jurisdictional Regulatory Exploitation | Exploiting inconsistencies and loopholes in regulations across different legal jurisdictions to conduct malicious activities that are difficult to prosecute. | ||||
BWC 1.5.5: Geopolitically-Induced Network Stress | The intentional or unintentional creation of extreme market volatility and network congestion stemming from major geopolitical events. This stress can cause cascading failures in critical on-chain and off-chain infrastructure, leading to mass liquidations, oracle failures, and protocol insolvency. | ||||
BWC 2: Access Control Vulnerabilities | BWC 2.1: Missing or Improper Authorization | BWC 2.1.1: Missing Access Control | Failure to implement any or sufficient authorization checks, allowing sensitive functions to be called by any user. | initialize() or setOwner() that was intended to be called only once but was left public. | onlyOwner).internal, private). |
BWC 2.1.2: tx.origin Authorization | Using tx.origin for authorization, which is insecure as it makes the contract vulnerable to phishing attacks where a user is tricked into calling a malicious intermediary contract. | A, which then calls the vulnerable contract B. Inside B, a check for tx.origin == victim_address passes, granting A the victim's privileges. | msg.sender for authorization, as it identifies the immediate caller. | ||
BWC 2.2: Flawed Permission Management | BWC 2.2.1: Unsafe Token Approvals | Granting excessive or indefinite token allowances (ERC20.approve) to smart contracts, which can lead to fund theft if the approved contract is compromised or malicious. | transferFrom to drain the user's wallet. | permit) for gasless, single-transaction approvals. | |
BWC 2.2.2: Misconfigured Proxy | Errors in deploying or managing proxy patterns (like Transparent or UUPS proxies) that can lead to storage collisions, lost implementations, or unauthorized upgrades. | ||||
BWC 2.2.3: Untrusted Arbitrary Calls | The contract allows an attacker to specify the target and calldata for a low-level call (e.g., .call()). This allows the attacker to force the contract to execute any action in its own context, effectively impersonating it. | token.transferFrom(victim, attacker, amount). Since the victim has approved the contract (BWC 2.2.1), the token contract accepts the request.token.transfer(attacker, amount) to drain assets held by the contract itself. | transferFrom or approve. | ||
BWC 2.2.4: Composable Arbitrary Calls | An exploit where composing multiple, individually secure contracts allows an attacker to make a contract perform a malicious, arbitrary call that would not be possible in isolation. | ||||
BWC 2.2.5: Ruggable Contract Design | Architectural design that intentionally allows privileged developers to steal or freeze user funds without warning. | ||||
BWC 2.3: Callback & Hook Vulnerabilities | BWC 2.3.1: Missing Validation in Callbacks | Failure to verify the caller or parameters of a public callback function. These functions (e.g., flashloan receivers, token hooks like onERC1155Received) must act as gatekeepers, but if they fail to authenticate that the caller is the specific trusted contract (e.g., the lending pool or the token contract), an attacker can invoke them directly to spoof events. | onERC1155Received or onERC721Received directly to simulate a deposit and trigger internal accounting logic (e.g., minting wrapper tokens) without actually transferring assets (e.g., the TSURU exploit). | msg.sender: Strictly verify that the caller is the expected token contract or lending pool address. | |
BWC 3: Smart Contract Logic & State Manipulation | BWC 3.1: Reentrancy Attacks | BWC 3.1.1: Standard Reentrancy | An attacker's contract calls back into a vulnerable contract before its state updates are completed, allowing for multiple withdrawals or other exploits. | nonReentrant). | |
BWC 3.1.2: ERC-777 Reentrancy | Exploiting token hooks in the ERC-777 standard (tokensToSend or tokensReceived) to reenter contracts during a token transfer. | tokensReceived hook on the malicious contract calls back into the victim contract. | |||
BWC 3.1.3: Read-only Reentrancy | Reentering a contract to read a state that is inconsistent or in the process of being changed, leading to logic errors, even if no state is written in the second call. | ||||
BWC 3.1.4: Composable Reentrancy | A reentrancy attack that becomes possible due to unforeseen interactions between multiple, otherwise secure, contracts. The vulnerability emerges from the composition of protocols. | ||||
BWC 3.2: Flawed State Management | BWC 3.2.1: Improper Initialization | Contracts deployed with incorrect initial state, missing initialization, or unset flags, often leaving them ownerless or in a vulnerable state. | initialize function on the implementation, allowing an attacker to claim ownership. | ||
BWC 3.2.2: Faulty Contract Checks | Logic errors in mechanisms that check the status or code of other contracts, such as verifying if an address is a contract or not. | extcodesize to check for an EOA, which can be bypassed if the check is performed during contract construction. | address.code.length > 0. | ||
BWC 3.2.3: Forced Ether Balance | Manipulating a contract's Ether balance to disrupt logic that depends on address(this).balance. | selfdestruct(victim_address). | address(this).balance for critical logic. Design contracts to be agnostic to their Ether balance. | ||
BWC 3.2.4: Self Transfers and Transaction Timing Attacks | Exploiting state changes caused by transfers to the same address or by the ordering of transactions within a block. | ||||
BWC 3.2.5: Broken State Adjustment | Errors in logic that are supposed to modify or correct contract state, leading to inconsistent or exploitable conditions. | ||||
BWC 3.2.6: Proxy/Contract Initialization Front-Running | An attacker observes a transaction that deploys a contract and immediately sends a transaction with a higher gas fee to initialize the contract with their own address as the owner. | initialize function before the legitimate deployer does. | |||
BWC 3.2.7: Broken Invariant via Function Overriding | A vulnerability created when a child contract inherits from a parent (e.g., an OpenZeppelin standard) and overrides an internal function. By altering the logic or removing critical checks in the overridden function, the child contract breaks the security assumptions (invariants) of other, non-overridden public functions in the parent contract that rely on the original internal function's behavior. | mint) in a parent contract that relies on an internal function (e.g., _deposit) for a critical check.deposit). | |||
BWC 3.2.8: Faulty Array & List Handling | Logic errors arising from the improper manipulation, validation, or searching of array data structures. This includes failing to sanitize inputs for duplicate entries or using search algorithms (like binary search) on arrays that violate uniqueness assumptions (e.g., duplicate timestamps), leading to incorrect accounting or stale data retrieval. | mapping to track processed items during iteration. | |||
BWC 3.3: Token Standard & Logic Issues | BWC 3.3.1: Double EntryPoint Tokens | Contracts where a native token also has an ERC-20 representation, potentially leading to inconsistent state or accounting if not handled carefully. | |||
BWC 3.3.2: Fee-on-Transfer & Rebase Accounting Issues | Incorrect handling of tokens that deduct fees during transfers or have an elastic supply (rebase tokens), leading to incorrect balance calculations. | X tokens, the recipient will receive X tokens, which is not true for fee-on-transfer tokens. | |||
BWC 3.3.3: Improper Handling of Native Tokens | Errors in managing the blockchain's native currency (e.g., ETH, BNB) alongside other tokens, often related to payable functions or msg.value. | msg.value or fails to check it, leading to over or underpayment. | msg.value in payable functions. | ||
BWC 3.3.4: Weird ERC20 Behaviors | Failure to handle non-standard implementations of the ERC20 interface, such as tokens that do not return a boolean on success for transfer or approve. | transfer on a non-compliant token, and the call succeeds but does not return true, causing the calling contract to revert. | SafeERC20 library, which handles these edge cases. | ||
BWC 3.3.5: EIP Standard Non-Compliance | A contract implements a feature based on a non-token EIP standard (e.g., ERC-3156 for flash loans, ERC-721 for NFTs) but deviates from the standard's required logic. This leads to broken interoperability with other compliant contracts and creates unexpected behaviors or logical flaws. | ||||
BWC 3.4: Governance & System Logic | BWC 3.4.1: DAO Governance Attacks | Exploiting voting mechanisms, proposal processes, or timelocks to pass malicious proposals or seize control of a protocol. | |||
BWC 3.4.2: Flawed Incentive Structures | Exploitable incentive structures or reward calculation errors that allow attackers to claim unfair rewards. This includes design flaws in penalty or slashing mechanisms where the funds are "donated" in a way that allows the penalized attacker to also be the beneficiary, effectively negating the penalty. | ||||
BWC 3.4.3: Bridge Status Mismatch | Inconsistencies between cross-chain bridge endpoints leading to fund loss or transaction failure, often due to one side of the bridge being paused or upgraded while the other is not. | ||||
BWC 4: Input & Data Validation Vulnerabilities | BWC 4.1: Insufficient Input Validation | BWC 4.1.1: Insufficient Input Validation | Failure to properly sanitize or validate transaction inputs, enabling malicious or unexpected data to be processed. This includes missing zero-address checks. | ||
BWC 4.2: Oracle Manipulation & Data Integrity | BWC 4.2.1: Insufficient Oracle Validation | Inadequate verification of external data feeds (e.g., price feeds), allowing manipulation of critical on-chain information. | |||
BWC 4.2.2: Oracle Manipulation | Actively compromising or gaming the data feeds that DApps rely on for external information, often by manipulating the price on a low-liquidity decentralized exchange that an oracle uses as its source. | ||||
BWC 4.3: Cryptographic Signature Flaws | BWC 4.3.1: Missing Signature Validation | Improper or missing verification of cryptographic signatures, enabling transaction forgery or replay attacks. | ECDSA library). | ||
BWC 4.3.2: Incomplete Signature Schemes | Flaws in the implementation of transaction signing cryptography, such as vulnerability to signature malleability or improper use of EIP-712. | ecrecover is not the zero address. | |||
BWC 4.4: Address Spoofing in Meta-Transactions | BWC 4.4.1: ERC-2771 + Multicall | A vulnerability where a contract uses both ERC-2771 for meta-transactions and a Multicall-type contract as its trusted forwarder. If the forwarder does not properly append the original caller's address to the callData of each sub-call, an attacker can control the data that the receiving contract mistakes for the caller's address, thus impersonating any account. | Multicall forwarder, crafting the callData of a sub-call so that its last 20 bytes contain the address of the victim they wish to impersonate (e.g., the contract owner).Multicall contract forwards this callData to the target contract without appending the real msg.sender.ERC2771Context, extracts the last 20 bytes of the received callData, trusting it to be the sender's address. It then grants the attacker the privileges of the impersonated victim. | msg.sender to the end of the callData for all sub-calls (e.g., abi.encodePacked(call.callData, msg.sender)).Multicall and ERC2771Context from libraries like OpenZeppelin, which have patched this specific interaction.Multicall contracts as trusted forwarders. | |
BWC 4.5: Inconsistent Data Interpretation | BWC 4.5.1: Parser Differential / Inconsistent Validation | Occurs when different components or execution paths interpret or validate the same input data differently. This creates a security gap where checks enforced in one context (e.g., immediate execution) are missing or implemented differently in another (e.g., retry logic, off-chain indexing vs on-chain execution). | |||
BWC 5: Economic & Game-Theoretic Vulnerabilities | BWC 5.1: Miner Extractable Value (MEV) Attacks | BWC 5.1.1: Front-Running | Placing a transaction in the queue before a known future transaction to exploit the order of execution. This is often possible when a transaction's input data contains sensitive information (like a password or a solution to a puzzle) that is publicly visible in the mempool. | ||
BWC 5.1.2: Back-Running | Placing a transaction immediately after a targeted transaction to exploit its effects. | ||||
BWC 5.1.3: Sandwich Attacks | Combining front-running and back-running to trap a victim's transaction and extract value. | ||||
BWC 5.2: Price & Liquidity Manipulation | BWC 5.2.1: Price Manipulation | Artificially influencing asset prices through coordinated market actions to exploit DApp mechanisms, liquidate other traders, or create false impressions of market activity. | |||
BWC 5.2.2: First Deposit / Inflation Attack | Exploiting initialization or low-liquidity conditions in liquidity pools or token vaults (e.g., ERC4626) to manipulate the share price and claim a disproportionate share of assets. | ||||
BWC 5.2.3: Hardcoded or Assumed Asset Price | Using a fixed, hardcoded price for an asset, or implicitly assuming a fixed price ratio (e.g., assuming 1 USDC = 1 USD), instead of using a dynamic oracle feed. This creates arbitrage opportunities when the asset's real market price deviates from the assumed price. | ||||
BWC 5.2.4: Over-Leverage & Liquidation Spirals | The protocol's design encourages or allows for excessive leverage, making the system fragile and susceptible to cascading liquidations ("death spirals") during periods of high market volatility. The risk is amplified when the collateral used is itself volatile, illiquid, or subject to de-pegging. | ||||
BWC 5.3: Transaction Execution Risks | BWC 5.3.1: Lack of Slippage Control | Missing or insufficient protection against price movement between the time a transaction is submitted and when it is executed, making it vulnerable to sandwich attacks. | |||
BWC 5.4: Systemic & Network-Level Economic Risks | BWC 5.4.1: Cascade Failure from Network Congestion | A systemic failure where extreme network congestion (leading to high gas fees) and rapid asset price volatility cause critical off-chain infrastructure (like oracles and keeper bots) to fail or lag. This can lead to cascading liquidations, failed auctions, or other unintended economic consequences because the system's assumptions about timely and affordable transaction inclusion are violated. | |||
BWC 6: Arithmetic & Numeric Vulnerabilities | BWC 6.1: Integer Overflow & Underflow | Exceeding the maximum or minimum value for an integer type, causing it to wrap around. | SafeMath for older Solidity versions. | ||
BWC 6.2: Precision Loss & Rounding Errors | Issues arising from integer division, order of operations (division before multiplication), or inconsistent decimal scaling. | ||||
BWC 6.3: Unsafe Type Casting | Improper or unchecked conversion between numeric types, potentially leading to overflow or precision loss. | uint256 to a uint128 without checking if the value fits, leading to truncation and unexpected behavior. | |||
BWC 6.4: Calculation Errors | General mathematical mistakes in contract logic, such as in liquidity or reward formulas. | ||||
BWC 6.5: Inconsistent Scaling Bugs | Occurs when a smart contract performs math on numbers that have different decimal precisions (e.g., mixing a token with 6 decimals and one with 18) without proper normalization. | ||||
BWC 7: Low-Level & EVM-Specific Vulnerabilities | BWC 7.1: Unchecked Return Values | Failing to verify the success status of external calls, leading the contract to incorrectly assume success when the call actually failed. | ERC20.approve() but doesn't check the boolean return value. The approval fails silently, but the contract proceeds as if it succeeded. | SafeERC20 library, which handles return value checks.success boolean returned from low-level calls. | |
BWC 7.2: Unsafe Storage & Memory Handling | BWC 7.2.1: Unsafe Storage Use | Improper handling of contract storage slots, leading to collisions or data corruption, especially in proxy patterns. | |||
BWC 7.2.2: Improper Deletion of Complex Types | Vulnerabilities arising from the improper deletion of complex data types (e.g., arrays of mappings, structs containing mappings). Operations like delete may not clear the underlying storage for nested mappings, leading to old data persisting and being misinterpreted later. | ||||
BWC 7.2.3: Broken EIP-1153 Transient Storage Use | Misuse of transient storage (TSTORE, TLOAD), which can enable reentrancy or state corruption due to improper clearing or assumptions about its lifecycle. | ||||
BWC 7.3: Weak Cryptographic Primitives | BWC 7.3.1: Weak Random Number Generation | Using predictable or manipulable sources of on-chain entropy (e.g., block.timestamp, blockhash). | block.timestamp to determine the winner, allowing a miner to influence the outcome. | ||
BWC 7.3.2: Malleable ecrecover | Vulnerabilities in signature recovery (ecrecover) allowing for signature reuse or forgery if not handled correctly. | ECDSA library, which protects against signature malleability. | |||
BWC 7.3.3: Second PreImage Attacks | Cryptographic vulnerabilities allowing for collisions in hash functions used by the contract, although this is generally considered infeasible with modern hash functions like SHA-256. | keccak256). | |||
BWC 7.3.4: Forgetting to Blind Polynomials in ZK Protocols | Weaknesses in zero-knowledge proof implementations that expose underlying data by failing to properly randomize cryptographic commitments. | ||||
BWC 7.3.5: Insecure Cryptographic Construction | Using sound cryptographic primitives (e.g., keccak256) but combining them in a way that creates a flawed or insecure algorithm. This is a design-level cryptographic flaw rather than a weakness in the primitive itself. | ||||
BWC 7.4: Client & Compiler Correctness | BWC 7.4.1: Incorrect VM Gas Charges | Logic that becomes vulnerable due to miscalculations of transaction execution costs or changes in gas costs from network upgrades. | |||
BWC 7.4.2: Compiler Bug | A bug in the compiler that causes it to generate incorrect bytecode, or vulnerabilities arising from improper compiler version management. | ^0.8.0) allows a contract to be deployed with different compiler versions, some of which may contain bugs. | pragma solidity 0.8.21;) in source code to ensure deterministic builds. | ||
BWC 8: Denial of Service (DoS) Vulnerabilities | BWC 8.1: DoS via External Calls | Blocking contract functionality through external calls to malicious or non-functional contracts. This often occurs when using low-gas-forwarding functions like .transfer() to send Ether to a contract that requires more gas for its fallback function than is provided. | .transfer() or .send() to a smart contract wallet (e.g., Gnosis Safe) whose fallback function consumes more than the 2300 gas stipend, causing the transaction to revert. | .transfer() and .send() for sending Ether..call{value: ...}("") instead, as it forwards all available gas. | |
BWC 8.2: DoS via Malicious Receivers | A recipient contract designed to revert or consume excessive gas when receiving tokens or Ether, causing the sender's transaction to fail. | ||||
BWC 8.3: DoS via Non-Reentrant Locks | Exploiting reentrancy guards to permanently or temporarily lock functions if the lock is not properly cleared on all execution paths. | try/catch blocks to ensure reentrancy locks are always cleared, even if an external call fails. | |||
BWC 8.4: DoS via Numeric Calculation | Causing numeric underflows, overflows, or division-by-zero errors that block contract execution. | ||||
BWC 8.5: DoS via Block Gas Limit | Crafting operations that exceed the block gas limit, making certain state transitions impossible, often by making an array or loop too large. | ||||
BWC 8.6: DoS via Hook Griefing | Exploitation of token standard callbacks (e.g., ERC777/721/1155) to cause denial of service by making them revert. | onERC721Received hook, preventing transfers to that address. | |||
BWC 8.7: DoS via Return Data Bomb | Exploitation of unbounded return data from an external call to cause an out-of-gas error when the data is copied to memory. | ||||
BWC 8.8: DoS in Cross-Chain Messaging Protocols | Specific vulnerabilities in protocols like LayerZero or their integrations that can halt message passing or cause messages to be delivered incorrectly. | ||||
BWC 8.9: DoS via Unreliable On-Chain Checks | A denial-of-service attack where an attacker exploits unreliable on-chain data sources or checks to block critical operations. A common example is manipulating the state of an address to make a check like address.codehash return an unexpected value, thereby preventing contract deployment. | bytes32(0) to keccak256(""). | address.codehash to determine if a contract exists. A more reliable check is address.code.length > 0. | ||
BWC 8.10: DoS via Forced Recursion | Occurs when a contract uses a recursive function (a function that calls itself) to iterate through a data structure. An attacker manipulates the contract's state to create an excessively long chain of data (e.g., nodes in a tree, linked list), forcing the recursive function to exceed the EVM's call stack limit (1024 frames). This causes any transaction calling the function to fail, permanently locking funds or functionality. | for, while) over recursive patterns. Iteration does not consume the call stack and is not vulnerable to this attack. | |||
BWC 8.11: DoS via Front-Running (Griefing) | Blocking a user's valid transaction by front-running it to alter the underlying state conditions required for success. Unlike MEV, the attacker does not necessarily profit; the goal is to cause the victim's transaction to revert. A common vector is "Permit Griefing," where an attacker observes a transaction containing a signed permit, extracts the signature, and submits it independently. The permit is executed, consuming the nonce. When the victim's transaction attempts to execute the permit again, it reverts due to the invalid nonce, failing the entire operation. | permit() by submitting the signature separately, causing the user's batch transaction to revert. | permit() in a try/catch block. If the call fails (e.g., nonce already used), verify if the allowance is sufficient and proceed. | ||
BWC 9: Emerging Technology Vulnerabilities | BWC 9.2: AI/ML Integration Attacks | BWC 9.2.1: AI Model Poisoning & Bias Exploits | Vulnerabilities arising from the corruption of an AI/ML model's training data or the exploitation of its inherent biases. This is an attack on the integrity of the model itself. | ||
BWC 9.2.2: AI Prompt Injection & Data Exfiltration | Occurs when a system allows untrusted external data (e.g., emails, calendar invites, web pages) to be interpreted as trusted commands by an AI agent. The AI is "jailbroken" by malicious data, causing it to perform unauthorized actions or leak sensitive information. | ||||
BWC 9.3: Hardware-Level Exploits | Attacks that target the underlying hardware on which nodes or validators run, such as Rowhammer or Spectre, to corrupt memory or leak sensitive data. | ||||
BWC 10: Network & Consensus Evolution Attacks | BWC 10.1: Advanced P2P Network Attacks | Sophisticated attacks on the peer-to-peer networking layer of a blockchain, such as eclipse attacks or network partitioning, to isolate nodes or disrupt consensus. | |||
BWC 10.2: Novel Consensus Mechanism Exploits | Vulnerabilities specific to newer or more complex consensus mechanisms beyond traditional Proof-of-Work or Proof-of-Stake. | ||||
BWC 10.3: Cross-Protocol Interoperability Attacks | Vulnerabilities that emerge from the complex and often unaudited interactions between different blockchain protocols, especially in the context of DeFi composability. | ||||
BWC 10.4: Protocol Upgrade-Induced Vulnerabilities | Vulnerabilities that emerge in previously secure contracts when a network or protocol upgrade (like an EIP implementation) changes the behavior or security assumptions of the underlying platform. The contract code itself doesn't change, but its execution context does, rendering existing security patterns ineffective. | ||||
BWC 10.4.1: EIP-7702 Delegation Risks | With the adoption of EIP-7702, Externally Owned Accounts (EOAs) can temporarily delegate their capabilities to a smart contract. This blurs the line between EOAs and contracts, breaking fundamental security assumptions. For example, the invariant that tx.origin is always an EOA is no longer true, rendering checks like msg.sender == tx.origin unsafe for reentrancy protection. | msg.sender == tx.origin true, bypassing old reentrancy guards.chain_id=0. | nonReentrant modifier) instead of tx.origin checks.initWithSig) or restricting calls to the ERC-4337 EntryPoint.CREATE2 and avoid chain_id=0. | ||
BWC 10.4.2: Constantinople Reentrancy (Deprecated) | A reentrancy vector introduced by a proposed change to SSTORE gas costs in EIP-1283 for the Constantinople hard fork. This change would have made .send() and .transfer() unsafe, breaking a core security assumption for many contracts. The hard fork was delayed to remove this vulnerability. | .send() or .transfer() to call back into the victim contract with enough gas to perform malicious state changes. | |||
BWC 10.4.3: Call Depth Attack (Deprecated) | A historical DoS vector, mitigated by the EIP-150 hard fork, where an attacker could recursively call a contract to exhaust the 1024 call depth limit, causing any subsequent external calls within the transaction to fail. | ||||
BWC 11: Privacy & Regulatory Attack Vectors | BWC 11.1: Privacy Protocol Compromises | BWC 11.1.1: Anonymity Set Failures | The effectiveness of a privacy protocol (especially mixers) relies on a large and diverse set of users to create a "crowd" to hide in. When the number of users or the volume of transactions is low, the anonymity set shrinks, making it easier for observers to statistically link deposits and withdrawals. | ||
BWC 11.1.2: Privacy OPSEC Failures | User-side errors in operational security that undermine the privacy protections offered by a protocol. Even a perfectly designed privacy protocol can be rendered ineffective if the user fails to follow best practices for maintaining their anonymity. | ||||
BWC 11.2: Regulatory Weaponization | BWC 11.2.1: Patent Trolling | Using patents, often acquired for the sole purpose of litigation, to file infringement lawsuits against open-source protocols or developers. The goal is typically to stifle competition, extract settlement fees, or create legal uncertainty, rather than to protect a genuine invention. | |||
BWC 11.2.2: Government Overreach | The use of state power, including sanctions, subpoenas, or regulatory enforcement actions, to target protocols, developers, or users in a manner that exceeds clear legal mandates or stifles innovation. | ||||
BWC 11.2.3: "Code is Law" Defense Exploitation | An attacker performs an economically harmful exploit and subsequently uses the legal argument that their actions were permissible because they were allowed by the smart contract's code. This strategy exploits the difficulty legal systems face in applying traditional statutes for fraud or manipulation to autonomous, decentralized protocols. |
General Principles & Mitigations
This section outlines high-level principles and common technical mitigations that apply broadly across many vulnerability classes. Specific, targeted mitigations can be found in the main table.
Core Security Principles
- Defense in Depth: Assume breach. Layer multiple, independent defenses so the failure of one does not compromise the whole system.
- Minimize Attack Surface: Every line of code is a liability. Reduce complexity by eliminating non-essential features, code, and dependencies to shrink the target for attackers.
- Least Privilege: Grant the absolute minimum permissions for the shortest time necessary. Limit both the scope (what) and duration (how long) of any privilege.
- Security as a Process: Security is a continuous process, not a one-time audit. Actively adapt defenses to the evolving threat landscape through ongoing review and learning.
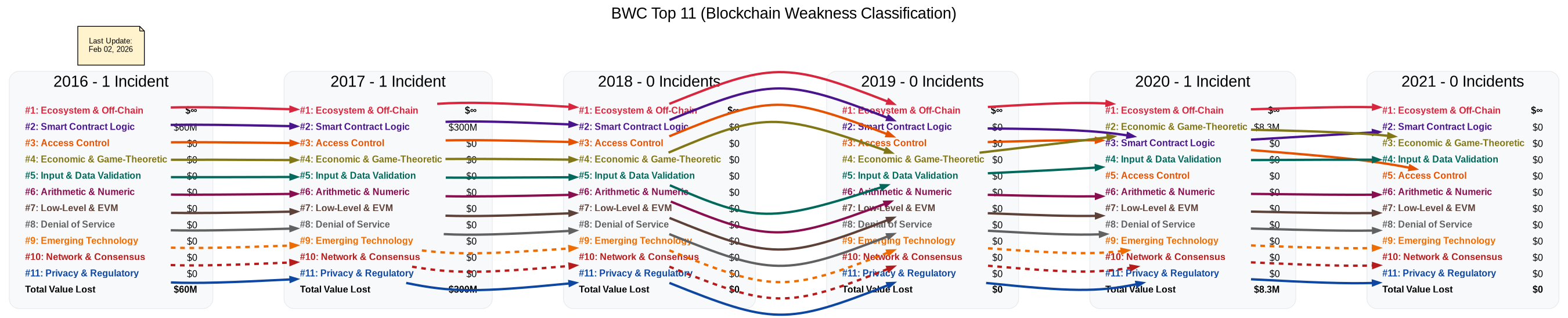
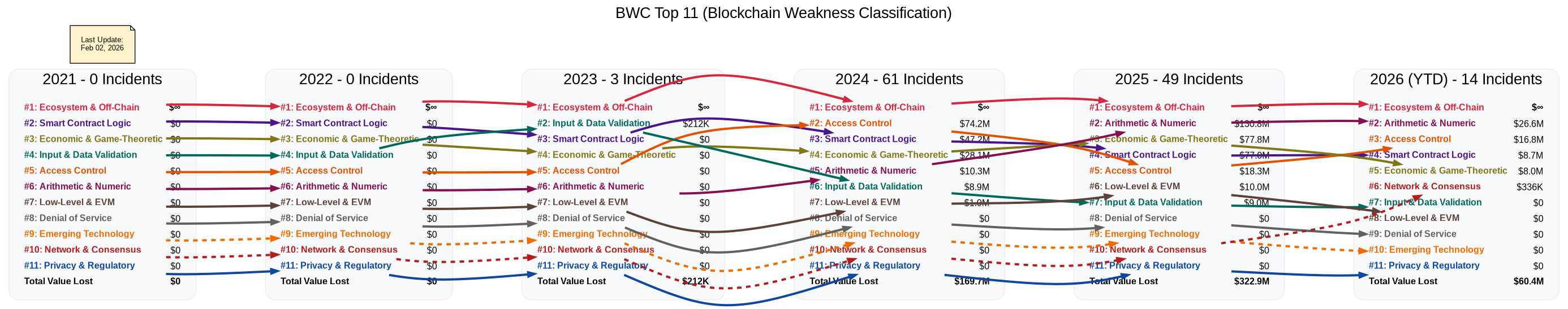
2026 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2026-02-02 - 14
- Date: 2026-02-02
- Project: Matcha Meta (SwapNet)
- Value Lost: ~$16,800,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.3: Untrusted Arbitrary Calls - Secondary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description:
- Matcha Meta's SwapNet router was exploited for ~$16.8M (later analysis suggests ~$17M) due to an arbitrary call vulnerability in a closed-source contract.
- Vulnerability: The SwapNet router failed to validate inputs properly, allowing unauthorized arbitrary calls. The attacker used this to force the contract to call
transferFromon various tokens, draining funds from users who had granted infinite approvals to the router. - Attack Flow:
- Reconnaissance: The attacker identified users with infinite approvals to the SwapNet router.
- Execution: The attacker exploited the arbitrary call flaw to inject calls to
token.transferFrom(victim, attacker, amount), bypassing the router's intended logic. - Laundering: Funds were swapped for USDC (~$10.5M) and then ~3,655 ETH on Base, which was subsequently bridged to Ethereum Mainnet.
- References:
2026-01-26 - 13
- Date: 2026-01-26
- Project: Individual Swap Incident (Illiquid Pool)
- Value Lost: ~$140,000
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.3.1: Lack of Slippage Control - Secondary Classification:
BWC 1.3.7: Flawed Off-Chain Infrastructure (Potential UI/Routing Failure)
- Broader Classification:
- Description:
- An individual user suffered a catastrophic loss of ~$140,000 in a single swap transaction, receiving only ~0.09 EUR in return.
- Vulnerability: The transaction was executed through a liquidity pool with insufficient depth (illiquid). The user's transaction likely lacked a proper
amountOutMin(slippage protection) parameter, or the interface used failed to warn/prevent the routing through the empty pool. - Execution: The user attempted to swap a high-value amount of tokens. Due to the lack of liquidity in the selected pool, the trade suffered ~100% price impact. Without a slippage revert, the transaction executed, effectively donating the funds to the pool's liquidity providers or back-running MEV bots.
- References:
2026-01-11 - 12
- Date: 2026-01-11 (Estimated based on report timing)
- Project: MetaverseToken (MT)
- Value Lost: ~$37,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- TenArmor detected a suspicious attack involving the MetaverseToken (MT) on BSC, resulting in a loss of approximately $37,000.
- Vulnerability: Limited details were provided, but the incident has been classified as price manipulation based on the detected on-chain behavior.
- Attack Flow: The specific mechanics involved an interaction with the MT contract that drained funds, likely via market manipulation or a flaw in how the token handles price/value calculations.
- References:
2026-01-01 - 11
- Date: 2026-01-01
- Project: Valinity
- Value Lost: ~$63,000
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures (Flawed Rebalance Logic) - Secondary Classification:
BWC 5.2.1: Price Manipulation (Spot Price Dependency)
- Broader Classification:
- Description:
- Valinity was exploited for ~$63k due to a business logic flaw in its rebalancing mechanism.
- Vulnerability: The
acquireByLTVDisparityfunction, intended to rebalance the syntheticVYtoken holdings based on LTV ratios and Uniswap V3 spot prices, was publicly callable. Crucially, the logic was flawed as it was hardcoded to execute swaps ofVYinto a liquidity pool that held negligible liquidity (~$106 USDC). - Attack Flow:
- Price Manipulation: The attacker swapped USDC for PAXG to artificially increase the PAXG price on Uniswap V3.
- Forced Dump: The attacker called the public
acquireByLTVDisparityfunction. Due to the inflated PAXG price (which altered the LTV calculation), the contract logic triggered a sell-off ofVYtokens into the illiquid pool. - Arbitrage/Borrow: The attacker bought the dumped
VYtokens cheaply from the pool and used them as collateral to borrow hard assets (ETH, BTC, PAXG) from the protocol, exiting with the profit.
- Note: The protocol paused contracts following the exploit.
- References:
2026-01-01 - 10
- Date: 2026-01-01
- Project: PRXVTai
- Value Lost: ~$97,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures (Reward Accounting Mismatch) - Secondary Classification:
BWC 2.3.1: Missing Validation in Callbacks (Missing Token Transfer Hooks)
- Broader Classification:
- Description:
- PRXVTai was exploited for ~$97k on Base due to a flaw in its staking reward mechanics.
- Vulnerability: The
PRXVTStakingcontract minted a transferable receipt token (stPRXVT) representing stakedAgentTokenV2. However, the contract failed to implement the necessary hooks (e.g.,_beforeTokenTransfer) to update reward accounting state variables when these receipt tokens were transferred between users. - Attack Flow:
- Staking/Transfer: The attacker likely staked tokens to receive
stPRXVTor transferredstPRXVTbetween wallets. - Accounting Desync: Because the reward logic (
earned()) calculated rewards based on the current balance but the "reward debt" (oruserRewardPerTokenPaid) was not synchronized during transfers, the system failed to correctly track how long the tokens were held by specific addresses. - Drain: This allowed the attacker to claim inflated rewards, which were then bridged to Ethereum.
- Staking/Transfer: The attacker likely staked tokens to receive
- References:
2026-01-20 - 9
- Date: 2026-01-20
- Project: SynapLogic
- Value Lost: ~$88,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.8: Faulty Array & List Handling (Duplicate Entries) - Secondary Classification:
BWC 3.4.2: Flawed Incentive Structures
- Broader Classification:
- Description:
- SynapLogic on Base was exploited for ~$88k due to a logic flaw in its referral system.
- Vulnerability: The
swapExactTokensForETHSupportingFeeOnTransferTokensfunction accepted a user-supplied arrayaddress[] refByto distribute referral rewards (10% per referee) but failed to check for duplicate addresses or cap the total payout percentage. - Attack Flow:
- Duplicate Injection: The attacker called the function with the
refByarray containing their own address repeated 31 times (e.g.,[self, self, ... x31]). - Reward Multiplication: The contract calculated the reward as 31 * 10% = 310% of the input value.
- Drain: The contract paid out the inflated reward in ETH/USDC from its reserves to the attacker, draining the purchasing contract.
- Duplicate Injection: The attacker called the function with the
- Note: The attacker also minted SYP tokens during the process, but these were locked in vesting and could not be sold. The profit was derived solely from draining the contract's liquidity backing the referral payouts.
- References:
2026-01-20 - 8
- Date: 2026-01-20
- Project: MakinaFi
- Value Lost: ~$4,130,000 (1,299 ETH)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation (Asset Inflation) - Secondary Classification:
BWC 4.2.2: Oracle Manipulation (Internal Accounting as Oracle)
- Broader Classification:
- Description:
- MakinaFi's DUSD Machine was exploited for ~$4.13M due to a vulnerability in its internal accounting logic.
- Vulnerability: The protocol used a specific Weiroll script to calculate the value of its positions (specifically in the MIM-3CRV Curve pool) to determine the Assets Under Management (AUM). This script relied on spot values that could be manipulated.
- Attack Flow:
- Manipulation: The attacker used large flash loans to inflate the value of the MIM-3CRV pool and the associated rewards.
- AUM Update: The attacker called
updateTotalAum, which ran the vulnerable script. This recorded an artificially inflated value for the protocol's holdings, consequently spiking the price of the DUSD token (which is derived from AUM). - Extraction: The attacker utilized the DUSD/USDC Curve pool (which relies on this internal price) to swap DUSD for USDC at the inflated rate.
- Execution Twist: The original attacker (0x2F93...) deployed the exploit contract but was front-run by an MEV bot (0x935...). The MEV bot replicated the attack logic and secured the funds.
- Status: The protocol is paused (Recovery Mode). The team is negotiating with the MEV builder and a Rocket Pool validator who unintentionally received a portion of the funds to recover the assets.
- References:
2026-01-21 - 7
- Date: 2026-01-21
- Project: SagaEVM (Saga Protocol Chainlet)
- Value Lost: ~$6.8M bridged to Ethereum)
- Chain: SagaEVM / Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment (Infinite Mint) - Secondary Classification:
BWC 10.3: Cross-Protocol Interoperability Attacks (IBC Message Validation)
- Broader Classification:
- Description:
- SagaEVM, an EVM-compatible chainlet of the Saga Protocol, was exploited for approximately $7 million, resulting in a chain halt at block height 6593800. The exploit targeted the ecosystem's stablecoin, Saga Dollar ($D).
- Vulnerability: The flaw existed within the chain's precompile bridge contract responsible for handling Inter-Blockchain Communication (IBC). The system failed to properly validate custom payloads, allowing a malicious helper contract to bypass collateral checks and mint infinite $D tokens "out of thin air."
- Attack Flow:
- Injection: The attacker deployed a malicious helper contract (0x7D69...) on SagaEVM.
- Infinite Mint: The helper contract sent crafted IBC messages to the precompile bridge, triggering the unauthorized minting of ~$7M in $D.
- Extraction: The attacker bridged the illicitly minted $D to Ethereum Mainnet via the Squid Router.
- Laundering: On Ethereum, the funds were swapped via 1inch and KyberSwap into ETH (2,000+ ETH), USDC, yUSD, and tBTC. A portion ($800k) was deposited into Uniswap V4 liquidity positions (NFTs).
- Status: SagaEVM remains paused. The Saga SSC mainnet and other chainlets were unaffected. The $D token depegged ~25% following the inflation event.
- Addresses:
- Attacker (Saga/ETH):
0x2044697623AfA31459642708c83f04eCeF8C6ECB - Malicious Helper Contract (Saga):
0x7D69E4376535cf8c1E367418919209f70358581E
- Attacker (Saga/ETH):
- References:
2026-01-12 - 6
- Date: 2026-01-12
- Project: YO Protocol
- Value Lost: ~$3,710,000 (Covered by Protocol Treasury)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.3.1: Lack of Slippage Control - Secondary Classification:
BWC 1.3.7: Flawed Off-Chain Infrastructure
- Broader Classification:
- Description:
- YO Protocol suffered a loss of ~$3.71M during a routine rebalancing operation due to a misconfigured automated swap. The protocol's "Automated Harvesting System" attempted to swap ~$3.84M worth of stkGHO for USDC but received only ~$112k, resulting in a 97% loss.
- Vulnerability: The incident was an operational failure rather than a smart contract exploit. The vault operator (keeper bot) submitted a transaction to the Odos Router with an effectively disabled slippage parameter (set to
17,872,058). The on-chain harvesting logic checked for "execution drift" but failed to validate the sanity of the initial output quote. - Execution: The aggregator, following the permissive instructions, routed the massive trade through fragmented and illiquid Uniswap V4 pools (and others including Curve/Balancer). The route utilized pools with extreme fee tiers (up to 88%) and insufficient liquidity, vaporizing the funds into the hands of LPs positioned in these pools.
- Incident Response: The YO Protocol team utilized their multisig to backstop the loss, purchasing ~3.71M GHO via CoW Swap (which offers MEV protection) and redepositing it into the vault. An on-chain message was sent to the LPs requesting a return of funds in exchange for a 10% bounty.
- References:
2026-01-12 - 5
- Date: 2026-01-12
- Project: dHEDGE
- Value Lost: $0 (Critical Vulnerability Patched; >$10M Risk)
- Chain: Ethereum / Optimism
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.5.1: Parser Differential / Inconsistent Validation - Secondary Classification:
BWC 10.3: Cross-Protocol Interoperability Attacks
- Broader Classification:
- Description:
- A critical vulnerability was identified in dHEDGE’s 1inch integration guard that could have allowed a malicious pool manager to bypass slippage protection and drain over $10M in user funds.
- Vulnerability: The issue stemmed from a Parser Differential between the dHEDGE contract guard and the 1inch Router. The dHEDGE guard calculated slippage based on the
tokeninput parameter provided in the function call. However, the 1inchunoswapfunction for Uniswap V3 pools ignores thistokeninput entirely, determining the swap direction (ZeroForOne) solely based on a specific bitmask within thepooluint256 identifier. - Attack Flow:
- Parser Deception: A malicious manager provides a worthless "Fake Token" as the
tokeninput. The dHEDGE guard calculates slippage logic based on this Fake Token (which the attacker controls to ensure checks pass). - Execution Divergence: The manager constructs the
poolidentifier such that the 1inch Router executes a swap of the real pool assets (e.g., USDT) -> Fake Token, ignoring thetokeninput provided in step 1. - Bypass: Because the dHEDGE guard logic assumes the Fake Token is the source asset being swapped, it fails to validate the slippage/outflow of the real USDT, allowing the manager to drain the pool.
- Parser Deception: A malicious manager provides a worthless "Fake Token" as the
- Incident Response: The vulnerability was disclosed by a whitehat researcher following an audit contest where it was initially missed. The protocol developers confirmed the severity and patched the issue before any exploitation occurred.
- References:
2026-01-08 - 4
- Date: 2026-01-08
- Project: TMXTribe
- Value Lost: ~$1,400,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures - Secondary Classification:
BWC 1.1.2: Barriers to Verification (The Specialist Gap)
- Broader Classification:
- Description:
- TMXTribe, a GMX fork, was exploited for approximately $1.4M over a 36-hour period due to flawed logic in its unverified contracts. The attack involved a loop of minting and staking TMX LP tokens using USDT, swapping the deposited USDT for USDG (the protocol's stablecoin), unstaking, and draining the acquired USDG.
- Vulnerability: The specific root cause was a logic bug in the LP staking and swapping mechanics that failed to account for this extraction loop. The contracts were unverified, hiding the exact flaw from independent review.
- Incident Response: Despite the exploit continuing for 36 hours, the team failed to pause the protocol. On-chain activity showed the team deploying and upgrading contracts during the attack but taking no effective action to stop the drainage.
- Addresses:
- Exploiter 1:
0x763a67E4418278f84c04383071fC00165C112661 - Exploiter 2:
0x16Ed3AFf3255FDDB44dAa73B4dE06f0c2E15288d
- Exploiter 1:
- References:
2026-01-08 - 3
- Date: 2026-01-08
- Project: Truebit
- Value Lost: ~$26,600,000
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.1: Integer Overflow & Underflow
- Broader Classification:
- Description:
- Truebit was exploited for approximately $26.6M due to an integer overflow vulnerability. A malicious actor was able to mint tokens for 0 ETH and subsequently swap them for 8,535 ETH.
- Vulnerability: The
getPurchasePrice()function, responsible for calculating the minting cost, relied on an internal calculation where intermediate values (v9 + v12) overflowed2^256. This overflow caused the price calculation to wrap around and result in zero (after division), allowing the attacker to mint TRU tokens for free. - Attack Flow: The attacker called
AdminUpgradeabilityProxy.buyTRU()to mint 240M tokens for 0 ETH, then calledsellTRU()to drain ETH from the protocol. This process was repeated with increasing amounts. - Addresses:
- Exploiter 1:
0x6C8EC8f14bE7C01672d31CFa5f2CEfeAB2562b50 - Exploiter 2:
0xc0454E545a7A715c6D3627f77bEd376a05182FBc - Protocol Contract:
0x764C64b2A09b09Acb100B80d8c505Aa6a0302EF2
- Exploiter 1:
- References:
2026-01-06 - 2
- Date: 2026-01-06
- Project: IPOR Fusion (USDC Optimizer on Arbitrum)
- Value Lost: ~$336,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 10: Network & Consensus Evolution Attacks - Primary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- A legacy IPOR Fusion vault (USDC on Arbitrum) was exploited for ~$336k. The exploit leveraged a "perfect storm" of a legacy vulnerability and a new attack vector introduced by EIP-7702.
- Vulnerability: The incident was caused by the combination of two factors:
- Legacy Logic Error: The specific legacy vault lacked strict validation for "fuses" (logic modules) in its
configureInstantWithdrawalFusesfunction, trusting that only verified addresses would add them. - EIP-7702 Delegation Hijack: An administrator account (
0xd8a1...) had delegated its execution to a helper contract (0xa3cc...) via EIP-7702. This helper contract contained a vulnerability allowing arbitrary calls.
- Legacy Logic Error: The specific legacy vault lacked strict validation for "fuses" (logic modules) in its
- Attack Flow:
- Identity Hijacking: The attacker exploited the arbitrary call vulnerability in the delegated helper contract to force the admin's EOA to call the Vault.
- Malicious Fuse Injection: Acting as the admin, the attacker added a malicious "fuse" to the vault.
- Drain: The attacker triggered
instantWithdraw, causing the vault to execute the malicious fuse code and transfer assets to the attacker.
- Incident Response: IPOR Labs acknowledged the exploit, confirmed it was isolated to this single legacy vault due to its unique configuration, and stated that the IPOR DAO would cover the shortfall from the treasury.
- References:
2026-01-03 - 1
- Date: 2026-01-03
- Project: Flow Blockchain / deBridge / LayerZero
- Value Lost: Undetermined (Significant breakdown in cross-chain accounting; Specific transactions of ~$200k+ cited)
- Chain: Flow, Cross-chain
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary:
BWC 1.1.6: Unverifiable Outcomes(State finality was revoked by decree, not consensus rules). - Secondary:
BWC 1.1.1: Indispensable Intermediaries(The validators acted as "Landlords" deciding who retains assets, failing the Walkaway Test).
- Broader Classification:
- Description:
- Following an undisclosed exploit, the Flow Blockchain team executed a mandatory chain rollback to revert the network state. However, the team allegedly failed to coordinate this action with critical bridge providers (e.g., deBridge, LayerZero), leading to a catastrophic state desynchronization between Flow and the broader ecosystem.
- Centralization Risk: The decision to unilaterally roll back the chain highlights the risks of centralized governance in Layer-1 blockchains, where "finality" can be revoked by the operator.
- Bridge Mismatch (Double Spend & Loss): The rollback created a temporal paradox for cross-chain transactions processed during the rollback window:
- Bridged Out (Double Spend): Users who bridged funds out of Flow had their assets released on the destination chain. The rollback restored their balances on Flow to the pre-transfer state, effectively doubling their funds.
- Bridged In (Total Loss): Users who bridged funds into Flow had their assets locked on the source chain. The rollback erased the crediting transaction on Flow, leaving the users with no assets on either chain.
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2025 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2025-12-31 - 6
- Date: 2025-12-29
- Project: Multiple (e.g., Skep-pe) / "Anti-Rug" Vigilante Bot
- Value Lost: Variable (Deployer ETH Locked / Failed Launches)
- Chain: Ethereum
- Actor:
0x5c37ce78b79a09d211f3d35a617f980585e32b3c - BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.11: DoS via Front-Running (Griefing) - Secondary Classification:
BWC 3.2.1: Improper Initialization
- Broader Classification:
- Description:
- A sophisticated "vigilante" bot campaign was identified targeting new token launches (often categorized as "shitcoins") that utilize a specific initialization pattern.
- The Flaw: Many token contracts use a
startTradingoropenTradingfunction that unconditionally callsIUniswapV2Factory.createPair(). The factory reverts if a pair for the token combination already exists. - The Exploit: The bot monitors the mempool for deployers funding their token contracts with ETH in preparation for liquidity addition. The bot then front-runs the deployer's
openTradingtransaction by callingcreatePairon the Uniswap factory directly. - The Impact: When the deployer's transaction attempts to execute, it reverts because the pair now exists. This effectively "bricks" the launch. In many cases, the contracts lack a mechanism to rescue the ETH sent to the contract (or rely on
openTradingto move it), causing the deployer's initial liquidity funds to be permanently locked or "burned." - Code Snippet:
function openTrading() external onlyOwner() { require(!tradingOpen,"trading is already open"); uniswapV2Router = IUniswapV2Router02(0x7a250d5630B4cF539739dF2C5dAcb4c659F2488D); _approve(address(this), address(uniswapV2Router), _tTotal); // VULNERABILITY: The bot calls factory.createPair() before this transaction executes. // This causes the legitimate launch transaction to revert due to the pair already existing. uniswapV2Pair = IUniswapV2Factory(uniswapV2Router.factory()).createPair(address(this), uniswapV2Router.WETH()); uniswapV2Router.addLiquidityETH{value: address(this).balance}(address(this),balanceOf(address(this)),0,0,owner(),block.timestamp); IERC20(uniswapV2Pair).approve(address(uniswapV2Router), type(uint).max); swapEnabled = true; tradingOpen = true; }
- References:
2025-12-29 - 5
- Date: 2025-12-29
- Project: MSCST (Staking Contract) / GPC Token
- Value Lost: ~$129,900
- Chain: BSC
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control - Secondary Classification:
BWC 5.2.1: Price Manipulation(Atomic Sandwich)
- Broader Classification:
- Description:
- Note: This incident occurred in late 2025.
- The MSCST staking contract on BSC was exploited for ~$129.9k via an atomic sandwich attack facilitated by a public function.
- Vulnerability: The
releaseRewardfunction lacked access control, allowing any caller to trigger internal logic. Additionally, the function allowed the caller to specify afeeparameter (or implicitly used the contract's balance) to execute a swap. - Attack Flow:
- Flashloan & Dump: The attacker flashloaned GPC tokens and swapped them for BNB, lowering the price of GPC.
- Trigger Vulnerability: The attacker called
releaseRewardwith thefeeset to the contract's MSC balance. This function swapped MSC for GPC and transferred the GPC directly to the GPC/BNB liquidity pool (callingsync), effectively increasing the GPC reserves and further lowering the price (making GPC cheaper). - Arbitrage: The attacker swapped their BNB back for GPC at the artificially lowered price, profiting from the spread, and repaid the flashloan.
- References:
2025-12-24 - 4
- Date: 2025-12-24
- Project: EIP-7702 Delegatee Contract (Unnamed)
- Value Lost: ~$280,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 10: Network & Consensus Evolution Attacks - Primary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks(Initialization Front-Running) - Secondary Classification:
BWC 3.2.1: Improper Initialization
- Broader Classification:
- Description:
- An uninitialized EIP-7702 delegatee contract was exploited on BSC, resulting in a loss of approximately $280,000.
- Vulnerability: The contract, intended to serve as a code source for EIP-7702 delegations, was deployed without being initialized.
- Attack Flow: The attacker called the exposed initialization function to grant themselves the owner role of the delegatee contract. Once in control of the logic contract, they were able to manipulate the accounts that had delegated to it, effectively draining the funds from the delegators.
- Aftermath: The stolen funds (~95 ETH equivalent) were subsequently deposited into Tornado Cash.
- References:
2025-12-21 - 3
- Date: 2025-12-21
- Project: CHAR (Token Pair)
- Value Lost: ~$144,500
- Chain: BSC
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.1.2: Back-Running(MEV Skimming) - Secondary Classification:
BWC 1.1.7: User Disempowerment(Operational Error / "Fat Finger")
- Broader Classification:
- Description:
- A user or project team member suffered a loss of ~$144.5k involving the CHAR token on BSC.
- Vulnerability: This was an operational error rather than a smart contract flaw. The victim mistakenly transferred CHAR tokens directly to the Uniswap V2-style liquidity pair address instead of interacting with the router to swap them.
- Execution: The liquidity pool contract's balance became greater than its tracked reserves (sync mismatch). An MEV bot detected this discrepancy and executed a transaction (likely calling
skim()or a swap) to extract the excess tokens, effectively claiming the "donated" funds.
- References:
2025-12-19 - 2
- Date: 2025-12-19
- Project: Dragun69
- Value Lost: ~$87,400
- Chain: BSC
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.3.3: Improper Handling of Native Tokens(Missingmsg.valueCheck) - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- Note: This incident occurred in late 2025 but was logged in the 2026 database due to disclosure/reporting timing.
- The "Dragun69: Router" contract on BSC was exploited for ~$87.4k due to a missing validation check on native token transfers.
- Vulnerability: The router's swap function (specifically for ETH -> Token swaps) failed to verify
msg.value. The contract logic assumed that the BNB amount specified in the swap parameters was provided by the caller in the current transaction. However, without the check, the contract utilized its own accumulated BNB balance to execute the swap. - Attack Flow:
- Trigger: The attacker called the Aggregator Proxy, which triggered the vulnerable implementation to run a PancakeV3 swap.
- Misappropriation: The router, failing to check
msg.value, spent its own WBNB/BNB reserves to fulfill the swap. - Extraction: The swap callback verified the balance and forwarded the resulting tokens/BNB to a recipient address specified in the untrusted calldata (the attacker), effectively draining the contract.
- Note: The project's deployments on Base and Ethereum were not affected as they correctly included the
msg.valuecheck. The BSC implementation was patched ~6 hours after the exploit.
- References:
2025-12-13 - 1
- Date: 2025-12-13
- Project: Ribbon Finance (Legacy Contracts / Opyn Fork)
- Value Lost: ~$2,700,000
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control(Unprotected Oracle Configuration/Ownership) - Secondary Classification:
BWC 4.2.2: Oracle Manipulation
- Broader Classification:
- Description:
- Note: This incident occurred in late 2025.
- Legacy contracts associated with Ribbon Finance (specifically an Opyn fork) were exploited for approximately $2.7M.
- Vulnerability: The root cause was identified as a flawed oracle upgrade. Approximately 6 days prior to the attack, the oracle pricer was updated. This update reportedly introduced an access control vulnerability (potentially involving an unprotected
transferOwnershipor insufficient checks on the pricer whitelist logic) that allowed the attacker to manipulate price-feed proxies. - Attack Flow:
- Market Creation: The attacker created a new option market (e.g., LINK/USDC) with a short expiration time.
- Oracle Manipulation: Abusing the vulnerable oracle stack, the attacker forced arbitrary expiry prices for assets like wstETH, AAVE, LINK, and WBTC into the shared Oracle at the specific expiry timestamp.
- Drain: The attacker redeemed large short oToken positions against the MarginPool. Because the MarginPool relied on the forged expiry prices for settlement, the attacker was able to drain WETH, wstETH, USDC, and WBTC.
- References:
2025-11-20 - 5
- Date: 2025-11-20
- Project: GANA Payment
- Value Lost: ~$3,100,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 10: Network & Consensus Evolution Attacks - Primary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks - Secondary Classification:
BWC 1.2.2: Private Key Leakage,BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description:
- GANA Payment, a newly launched payment protocol on BSC, was exploited for $3.1 million just nine days after launch.
- Root Cause: The exploit originated from a compromised owner private key. The attacker used this key to authorize an EIP-7702 delegation to a malicious contract.
- The Exploit: The malicious delegator contract acted as a middleman, allowing the attacker to bypass the
onlyEOA(tx.origin == msg.sender) check on the staking contract. Because the transaction was an EIP-7702 transaction authorized by the owner, the staking contract perceived the calls as legitimate EOA interactions from the owner. - Attack Flow:
- Access: Compromised the owner key.
- Delegation: Transferred ownership to 8 different addresses, each authorizing the malicious EIP-7702 delegator.
- Manipulation: The delegated code manipulated the
gana_Computilityreward rate to an astronomical value (10,000,000,000,000,000). - Drain: Systematically staked and unstaked funds through these accounts, draining the protocol.
- Aftermath: $2.1M was bridged to Ethereum, and ~$1M was laundered through Tornado Cash on BSC.
- References:
2025-11-11 - 4
- Date: 2025-11-11
- Project: @ImpermaxFinance
- Value Lost: 380,000 $
- Chain: base
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.2: Precision Loss & Rounding Errors - Secondary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description:
- The exploit was a sophisticated, multi-stage attack that combined a precision loss vulnerability in the liquidation mechanism with a missing access control on a fund allocation function.
- 1. Precision Loss & State Manipulation: The attacker repeatedly created tiny, "underwater" debt positions in a low-liquidity lending market (cbBTC). By calling the
restructureBadDebt()function, a rounding error allowed them to incrementally drain the market'stotalBalanceone wei at a time. This manipulation drove the pool'sexchangeRateto near zero. - 2. Triggering a Malicious State: The attacker continued this process until the pool's
totalBalancewas exactly zero. This triggered a fallback condition in the code where theexchangeRatefunction returned a default, artificially high value of1e18. At this point, the attacker held nearly 100% of the pool's shares, acquired for a negligible cost. - 3. Missing Access Control & Fund Drain: The attacker then exploited an unprotected
flashAllocatefunction in a separate lending vault contract. This function, which lacked proper access control, was used to force the main cbBTC vault to deposit all its funds into the attacker's manipulated, malicious pool. Due to the artificially high exchange rate, the vault received almost no shares for its large deposit. The attacker, holding all the shares, then withdrew the vault's funds.
- References:
2025-11-04 - 3
- Date: 2025-11-04
- Project: @MoonwellDeFi
- Value Lost: 1,000,000 $
- Chain: base
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.2.1: Insufficient Oracle Validation
- Broader Classification:
- Description: Moonwell DeFi's wrsETH price anomaly on November 4, 2025, stemmed from a Chainlink oracle malfunction. The protocol's vulnerability was its failure to validate the data received from its price oracle, blindly trusting an erroneously high price for wrsETH. An exploiter was able to repeatedly borrow over 20 wstETH with only ~0.02 wrstETH flashloaned and deposited due to the faulty oracle that returned a wrstETH price of
$5.8M. The attacker profited by approximately 295 ETH ($1M). - References:
2025-11-03 - 2
- Date: 2025-11-03
- Project: Balancer Hack Side Story (Sonic Chain)
- Value Lost: ~$3,000,000
- Chain: Sonic
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.5.1: Parser Differential / Inconsistent Validation - Secondary Classification:
BWC 10.3: Cross-Protocol Interoperability Attacks
- Broader Classification:
- Description:
- On November 3, 2025, following the Balancer V2 hack, the Sonic team attempted to contain the exploit by freezing the attacker's account on the L1 level. They set the attacker's native token balance to zero and replaced their code, intending to prevent them from paying gas to move funds.
- The Bypass (BWC 4.5.1): The attacker bypassed this "transport layer" freeze by exploiting an inconsistency between the L1 gas requirements and the application-level logic. The Beets Staked Sonic (stS) token supported ERC-2612
permit, which allows for gasless approvals via off-chain signatures. The attacker signed apermit(which requires no gas) to authorize a secondary wallet, then used that secondary wallet totransferFromand drain the "frozen" assets.
- References:
2025-11-03 - 1
- Date: 2025-11-03
- Project: Balancer V2 & Forks
- Value Lost: ~$120,000,000
- Chains: Ethereum, Base, Polygon, Sonic, Arbitrum, Optimism, Berachain, Gnosis, Avalanche.
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.2: Precision Loss & Rounding Errors - Secondary Classification:
BWC 1.1.2: Permissioning & Censorship Risks,BWC 5.1.1: Front-Running
- Broader Classification:
- Description:
- Arithmetic Vulnerability: The core of the exploit was a precision loss vulnerability within the
upscalefunction in Balancer V2's Composable Stable Pools. This function would incorrectly round down when scaling factors were non-integer values. An attacker utilized thebatchSwapfeature to execute a three-stage attack: first, they precisely adjusted a token's balance to a rounding boundary; second, they performed swaps with crafted amounts, causing the rounding error to deflate the calculated price of the Balancer Pool Tokens (BPT); finally, they swapped assets back to the artificially cheapened BPT for a significant profit. This method was replicated across multiple chains where Balancer V2 or its forks were deployed. - Censorship & Centralized Interventions: Following the exploit, several chains took centralized action. Berachain validators halted the network for a hard fork; Sonic Labs froze the attacker's wallet; Gnosis froze affected pools and suspended its bridge; and Polygon validators reportedly censored the attacker's transactions.
- Front-Running: A white-hat MEV bot operator successfully front-ran some of the attacker's transactions on Ethereum, recovering and returning approximately $600,000.
- Arithmetic Vulnerability: The core of the exploit was a precision loss vulnerability within the
- References:
2025-10-15 - 5
- Date: 2025-10-15
- Project: ZKsync OS
- Value Lost: $0 (Critical Vulnerability Found in Audit)
- Chain: ZKsync Era
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.7: DoS via Return Data Bomb - Secondary Classification:
BWC 1.1.1: Indispensable Intermediaries(L1->L2 Queue Halt)
- Broader Classification:
- Description:
- A critical denial-of-service vulnerability was identified in the ZKsync OS execution environment. The system preallocated a fixed 128 MB buffer for
return_datafrom external calls. - The Exploit: An attacker could craft a transaction that makes numerous external calls, returning large amounts of data. This would overflow the preallocated buffer (causing a panic) while remaining within the transaction's gas limit.
- Impact: Crucially, if this panic occurred within an L1->L2 transaction (which are processed sequentially in a queue), it would permanently halt the entire L1->L2 transaction queue. Since the queue processing halts on a panic, no subsequent L1->L2 transactions could ever be processed, effectively bricking the bridge.
- A critical denial-of-service vulnerability was identified in the ZKsync OS execution environment. The system preallocated a fixed 128 MB buffer for
- References:
2025-10-15 - 4
- Date: 2025-10-15
- Project: ZKsync OS
- Value Lost: $0 (Critical Vulnerability Found in Audit)
- Chain: ZKsync Era
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.4.5: Client Consensus Bug - Secondary Classification:
BWC 7.4.2: Compiler/Architecture Correctness
- Broader Classification:
- Description:
- A critical non-determinism bug was identified in ZKsync OS during an audit. The issue stemmed from the use of architecture-dependent
usizearithmetic in Rust. - The Flaw:
usizeis 32-bit on the ZK prover's RISC-V architecture but 64-bit on the sequencer's x86_64 architecture. - The Exploit Vector: An attacker could craft a transaction with calldata lengths close to
u32::MAX.- On the Sequencer (64-bit), the transaction processes successfully because the 64-bit integer does not overflow.
- On the Prover (32-bit), the same calculation overflows or panics.
- Impact: This discrepancy effectively breaks the "Client Consensus." The sequencer accepts a block that the prover cannot prove. If such a block were committed, it would halt the L1 verification process, potentially freezing the entire ZKsync Era network.
- A critical non-determinism bug was identified in ZKsync OS during an audit. The issue stemmed from the use of architecture-dependent
- References:
2025-10-10 - 3
- Date: 2025-10-10
- Project: Binance
- Value Lost: Unknown
- Chain: N/A (Centralized Exchange)
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.1.6: Closed-Source Design
- Broader Classification:
- Description: During a market crash, a trader's pair trade (one long, one short position) was liquidated in a seemingly adversarial manner. Instead of partially liquidating both positions to maintain the hedge, the exchange's closed-source liquidation engine allegedly closed the profitable short position entirely, while leaving the long position fully exposed to the market crash, leading to its complete liquidation shortly after. This highlights the risks of trading on platforms with opaque, unauditable liquidation systems that may prioritize the house's profit over optimal position resolution for the user.
- References:
2025-10-10 - 2
- Date: 2025-10-10
- Project: Multiple (Ethena Labs, Zerobase, Venus Protocol)
- Value Lost: ~$400B in total liquidations
- Chain: Not Specified
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.5.5: Geopolitically-Induced Network Stress - Secondary Classification:
BWC 5.4.1: Cascade Failure from Network Congestion,BWC 4.2.2: Oracle Manipulation
- Broader Classification:
- Description: The "Black Friday" event was a systemic failure triggered by a major geopolitical event (Trump's tariff announcement), which caused a crypto market plunge and led to a cascade of liquidations. The market crash led to mass liquidations, which in turn caused the depeg of USDe and the failure of the WBETH oracle, amplifying the crisis across multiple protocols. The Venus Protocol was directly impacted by an oracle failure when the price of WBETH depegged, highlighting the vulnerability of critical off-chain infrastructure during extreme market stress.
- References:
2025-10-04 - 1
- Date: 2025-10-04
- Project: Abracadabra (@MIM_Spell)
- Value Lost: ~$1,700,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description: The root cause was a flawed implementation in the
cookfunction, which allows users to execute multiple operations in a single transaction. The vulnerability occurred when an attacker combined two actions:ACTION_BORROW, which correctly set aneedsSolvencyCheckflag totrue, followed byACTION_CUSTOM, which called an empty helper function that incorrectly returned a fresh status object, resetting theneedsSolvencyCheckflag tofalse. This second action overwrote the critical security flag set by the first, effectively bypassing the solvency check and allowing the attacker to borrow millions in MIM tokens against zero collateral. - References:
2025-09-30 - 11
- Date: 2025-09-30
- Project: f(x) Protocol v2
- Value Lost: $0 (Funds lock-up)
- Chain: Not Specified
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.10: DoS via Forced Recursion
- Broader Classification:
- Description: A critical vulnerability was discovered during an audit that allowed an attacker to permanently lock user funds. The protocol used a recursive function to update user positions. An attacker could trigger around 150 insignificant liquidations, each creating a new node in a data structure. When a legitimate user later tried to manage their position, the recursive function would attempt to traverse this long chain of nodes, exceeding the EVM's call stack limit and causing the transaction to fail. This permanently prevented users from accessing their funds.
- References:
2025-09-30 - 10
- Date: 2025-09-30
- Project: Uniswap v4 Hooks (Conceptual)
- Value Lost: $0 (Conceptual bug pattern)
- Chain: Not Specified
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures
- Broader Classification:
- Description: A conceptual vulnerability in donation-based penalty mechanisms, as seen in a Uniswap v4 hook designed to penalize just-in-time (JIT) liquidity. The hook donates a penalized LP's fees to other in-range LPs. The flaw allows an attacker to bypass this penalty by using a secondary account to be the sole recipient of their primary account's "donated" penalty fees, effectively turning the penalty into a self-rebate.
- References:
2025-09-27 - 9
- Date: 2025-09-27
- Project: Cool
- Value Lost: $100,500
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control - Secondary Classification:
BWC 5.1.1: Front-Running
- Broader Classification:
- Description: A proxy contract was upgraded to a new implementation named "Cool". This new implementation contained a
withdrawToken()function that lacked proper access control. A transaction calling this unprotected function was subsequently front-run by an MEV bot, leading to the loss of all funds. - References:
2025-09-23 - 8
- Date: 2025-09-23
- Project: MYX Finance
- Value Lost: ~$73,000,000 (from liquidations)
- Chain: Not Specified
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 1.3.8: Sybil Attacks,BWC 1.2.3: Insider Threat
- Broader Classification:
- Description: A coordinated, multi-vector attack involving massive price manipulation and a large-scale Sybil attack. Attackers used 100 coordinated wallets to claim $170 million in an airdrop, securing a large supply of the token. They then generated billions in artificial volume (wash trading) and engineered a short squeeze that liquidated over $73 million from retail traders. The project's official response appeared to defend the Sybil attack, suggesting potential insider complicity.
- References:
2025-09-23 - 7
- Date: 2025-09-23
- Project: Base Sequencer Debate
- Value Lost: $0 (Ecosystem Risk)
- Chain: N/A (Off-Chain)
- BWC:
- Broader Classification:
BWC 11: Privacy & Regulatory Attack Vectors - Primary Classification:
BWC 11.2.2: Government Overreach
- Broader Classification:
- Description: This incident represents a case of Regulatory Weaponization, where ecosystem participants called for regulatory action against a competitor (Base) over technical disagreements about its sequencer design. The core of the issue involved intentionally mischaracterizing a novel technology (a transaction sequencer) by equivocating it with a known regulated entity (a traditional exchange's matching engine) in an attempt to invite SEC scrutiny.
- References:
2025-09-13 - 6
- Date: 2025-09-13
- Project: JUDAOGlobal (Tentative)
- Value Lost: $20,000,000
- Chain: Polygon
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.1: Improper Initialization - Secondary Classification:
BWC 2.2.2: Misconfigured Proxy
- Broader Classification:
- Description: A developer executed a faulty proxy upgrade, setting an incorrect implementation contract for a vault holding 77 million POL tokens from a presale. Crucially, the developer forgot to call the
initializefunction on the new implementation. This failure to re-initialize the contract's state effectively wiped out all admin and upgrade privileges, leaving the contract ownerless and the $20 million in funds permanently locked and inaccessible. - References:
- Locked Contract
- Flagged by: @YannickCrypto
2025-09-12 - 5
- Date: 2025-09-12
- Project: Shibarium Bridge
- Value Lost: ~$3,957,000
- Chain: Ethereum Mainnet, Shibarium
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.2.2: Private Key Leakage - Secondary Classification:
BWC 1.1.1: Centralization Risks
- Broader Classification:
- Description: A sophisticated attack compromised the Shibarium PoS bridge, resulting in the unauthorized withdrawal of multiple assets. The attacker gained control over the signing keys for 10 of the 12 network validators, allowing them to forge malicious checkpoint/exit proofs and approve fraudulent transactions. The root cause was a widespread compromise of validator keys. The incident highlighted significant centralization risks, as a majority of the validators were "internal" (operated by the core team) and their key compromise led to a catastrophic failure of the bridge's security model.
- References:
2025-09-10 - 4
- Date: 2025-09-10
- Project: NPM Supply Chain Attack
- Value Lost: ~$50
- Chain: Multiple (ETH, BTC, SOL, TRX)
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.4.4: Supply Chain Attacks - Secondary Classification:
BWC 1.3.1: Social Engineering Exploits
- Broader Classification:
- Description: A widespread supply chain attack was identified where an attacker compromised a reputable developer's NPM account via a targeted phishing email. The attacker then injected a malicious, obfuscated payload into popular NPM packages. This payload was designed to compromise front-end applications and browser wallets by intercepting network requests and silently swapping user crypto addresses with the attacker's address during transactions.
- References:
2025-09-10 - 3
- Date: 2025-09-10
- Project: Reth (Ethereum Client)
- Value Lost: $0
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.4.5: Client Consensus Bug
- Broader Classification:
- Description: A bug in the Reth Ethereum client's state root computation caused multiple nodes running this client to stall on the Ethereum mainnet. The flaw was not in a smart contract but in the client software itself, which failed to correctly compute the state root according to the protocol rules. This led to a consensus failure where the affected nodes could not agree on the state of the chain with the rest of the network, requiring operators to manually intervene.
- References:
2025-09-05 - 2
- Date: 2025-09-05
- Project: Uniswap vs. Bancor
- Value Lost: $Millions in legal fees
- Chain: Not Applicable (Legal/Off-Chain)
- BWC:
- Broader Classification:
BWC 11: Privacy & Regulatory Attack Vectors - Primary Classification:
BWC 11.2.1: Patent Trolling
- Broader Classification:
- Description: This incident is not a technical exploit but a legal one. The Bancor team filed a patent infringement lawsuit against Uniswap, claiming Uniswap's Automated Market Maker (AMM) violates their patent. This represents a case of Regulatory Weaponization, where the legal system is used to attack a competitor, stifle open-source innovation, and extract value, posing a systemic risk to the ecosystem.
- References:
2025-09-02 - 1
- Date: 2025-09-02
- Project: @bunni_xyz
- Value Lost: $ 8,400,000
- Chain: Ethereum, Unichain
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.2: Precision Loss & Rounding Errors - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- The exploit's root cause was a rounding error in the smart contract logic that updated a pool's idle balance during withdrawals. While the rounding direction was safe for single operations, it became exploitable when combined in a specific sequence.
- The attacker used a flash loan to perform a large swap, manipulating the price and draining most of one asset from a pool. They then executed a series of 44 tiny withdrawals. Each withdrawal exploited the rounding error, causing the protocol's tracked total liquidity to decrease disproportionately more than the tiny amount actually withdrawn.
- After corrupting the pool's internal accounting, the attacker executed a final large swap and reverse swap at the highly manipulated price, draining approximately $8.4M from the affected pools on Ethereum and Unichain.
- References:
2025-08-25 - 5
- Date: 2025-08-25
- Project: Panoptic
- Value Lost: $0 (White-hat rescue of over $4M)
- Chain: Ethereum, Base, Unichain
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.3.5: Insecure Cryptographic Construction - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- A critical vulnerability was discovered in Panoptic's "position fingerprinting" mechanism, which allowed an attacker to bypass all solvency checks and drain funds. The flaw stemmed from a combination of an insecure cryptographic construction and insufficient input validation.
- Cryptographic Weakness: The position fingerprint was generated by XORing the
keccak256hashes of individual position IDs. Using XOR as a combiner is cryptographically insecure, as it is vulnerable to collision attacks (e.g., via Gaussian elimination). - Insufficient Input Validation: The protocol failed to validate that the user-supplied position IDs in a list were legitimate or even owned by the caller.
- Attack Path: An attacker could craft a fraudulent list of arbitrary, non-existent positions that produced the same XOR fingerprint as a real, high-collateral position. By submitting this spoofed list, they could trick the contract into believing they were solvent, allowing them to withdraw collateral and drain funds.
- The vulnerability was responsibly disclosed by a researcher from Cantina, leading to a coordinated white-hat rescue operation that successfully secured over 98% of at-risk funds, preventing any loss.
- References:
2025-08-24 - 4
- Date: 2025-08-24
- Project: Unverified Staking Contract
- Value Lost: ~$85,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 10: Network & Consensus Evolution Attacks - Primary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- An unverified staking contract on BSC was exploited for ~$85k. The victim contract used the "EOA only" (
tx.origin == msg.sender) check to protect its stake function from flashloan-based price manipulation. - The Exploit: The attacker deployed a malicious contract and authorized its delegation to an EOA using a 7702-type transaction. The EOA transferred ~13.9 BNB tokens to itself, triggering arbitrary smart contract logic while ensuring that future
tx.origin == msg.senderchecks pass. - Attack Flow:
- Flashloan & Pump: In the fallback function, the malicious contract flashloaned $3.5M BSC-USD, bought POT tokens from the PancakeSwap BSC-USD/POT pool to inflate the price, then staked ~220k POT at the inflated price.
- Dump: The attacker swapped the remaining POT tokens back to BSC-USD tokens to repay the flashloan and almost reset the BSC-USD/POT price.
- Profit: In a subsequent transaction, the attacker unstaked and received 3.3M POT tokens (versus 220k staked) due to the inflated recorded value.
- An unverified staking contract on BSC was exploited for ~$85k. The victim contract used the "EOA only" (
- References:
2025-08-24 - 3
- Date: 2025-08-24
- Project: ShibaSwap Treasure Finder
- Value Lost: $27,000
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.1.3: Sandwich Attacks - Secondary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks
- Broader Classification:
- Description: The
convert()function in the ShibaSwap: Treasure Finder contract lacked slippage protection, enabling exploitation through sandwich attacks. Additionally, itsonlyEOA()modifier, intended to prevent contract calls, was bypassed using an EIP-7702 account, demonstrating a protocol upgrade-induced vulnerability. - References:
- Exploit Tx 1
- Flagged by: @TenArmorAlert
2025-08-23 - 2
- Date: 2025-08-23
- Project: RansomVault Hacker
- Value Lost: $90,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.1.1: Front-Running
- Broader Classification:
- Description: This incident involves a hacker's (Hacker A) ransomware contract being exploited by another attacker (Hacker B), likely an MEV bot. The
withdrawETHfunction was protected by a password that was passed as a cleartext argument in the transaction data. When Hacker A tried to withdraw the ransom, their transaction sat in the public mempool. Hacker B scanned the mempool, extracted the password, and submitted their own transaction with a higher gas fee to front-run Hacker A and steal the funds. - References:
2025-08-13 - 1
- Date: 2025-08-13
- Project: Coinbase
- Value Lost: $550,000
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description: Coinbase's fee-receiver wallet lost approximately $550,000 due to mistakenly granting ERC-20 allowances to 0x's Mainnet Settler, a permissionless execution contract. This was not a hack but a configuration error that handed a sophisticated MEV bot the approval to drain dozens of token types from Coinbase's treasury, as anyone can call the Settler contract.
- References:
- Exploit Tx
- Flagged by: @deeberiroz
2025-07-28 - 5
- Date: 2025-07-28
- Project: SuperRare
- Value Lost: $730,000
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description: The core of the vulnerability was a logically flawed
requirestatement intended to enforce access control. The coderequire((msg.sender != owner() || msg.sender != address(0xc2...)), "Not authorized...");always evaluates to true for any caller, because an address cannot be two different values simultaneously. This logical error rendered the authorization check completely ineffective, making it functionally missing. - References:
2025-07-15 - 4
- Date: 2025-07-15
- Project: Arcadia
- Value Lost: $3,600,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls
- Broader Classification:
- Description: The attacker exploited a missing validation vulnerability in the Asset Manager contracts. By supplying malicious calldata to a rebalancing function, the attacker tricked the Asset Manager into making an arbitrary call to a victim's Arcadia Account. Since the victim had authorized the Asset Manager, this call was successful, allowing the attacker to impersonate the Asset Manager and drain the victim's funds.
- References:
2025-07-09 - 3
- Date: 2025-07-09
- Project: GMX
- Value Lost: $42,000,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.1.4: Composable Reentrancy
- Broader Classification:
- Description: The GMX protocol was exploited via a sophisticated composable reentrancy attack. The vulnerability was in the
PositionManager.executeDecreaseOrder()function, which made an external call (an ETH refund) to the attacker's contract. The attacker's contract then re-entered the GMX protocol, opening a large leveraged position before the initial transaction was complete. This manipulation artificially inflated the Assets Under Management (AUM) of the GLP pool, allowing the attacker to redeem their own GLP tokens at a much higher price. - References:
2025-07-09 - 2
- Date: 2025-07-09
- Project: ZKSwap
- Value Lost: $5,000,000
- Chain: N/A
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.3.1: Missing Signature Validation
- Broader Classification:
- Description: The
verifyExitProof()function contained a hardcodedreturn true;statement, which effectively disabled the cryptographic verification of withdrawal proofs. An attacker activated the emergency "Exodus Mode" and repeatedly called theexit()function with fabricated proofs, which the contract accepted due to the skipped verification, allowing the attacker to drain funds. - References:
2025-07-02 - 1
- Date: 2025-07-02
- Project: Quickswap
- Value Lost: Unknown
- Chain: Polygon
- BWC:
- Broader Classification:
BWC 10: Network & Consensus Evolution Attacks - Primary Classification:
BWC 10.4.1: EIP-7702 Delegation Risks
- Broader Classification:
- Description: The contract implemented an
onlyEOA()modifier to prevent contract-based calls (like flash loans). An attacker leveraged an EIP-7702 transaction to bypass this check. EIP-7702 allows a contract to execute a call while setting themsg.senderto the EOA that signed the transaction. This made theonlyEOA()check returntrue, tricking the contract into believing the caller was a standard user while allowing the attacker to execute complex contract logic. - References:
2025-06-20 - 3
- Date: 2025-06-20
- Project: Unidentified Staking Contract
- Value Lost: ~$32,000
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.1: Unchecked Return Values - Secondary Classification:
BWC 3.3.4: Weird ERC20 Behaviors
- Broader Classification:
- Description: The staking contract was exploited due to its failure to check the return value of an external call to a legacy Compound cToken (cUSDC). An attacker called the deposit function, but the underlying
cUSDC.transferFromcall failed and returnedfalseinstead of reverting. The victim contract did not validate this boolean response and proceeded as if the deposit were successful, incorrectly updating the attacker's internal balance. The attacker was then able to withdraw real funds from the contract based on their unbacked, phantom deposit. - References:
- Exploit Tx
- Flagged by: @deeberiroz
2025-06-17 - 2
- Date: 2025-06-17
- Project: MetaPool (mpETH)
- Value Lost: $227,785
- Chain: Mainnet
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.7: Broken Invariant via Function Overriding
- Broader Classification:
- Description: The mpETH staking contract, which inherited from OpenZeppelin's
ERC4626Upgradeable, was exploited due to a broken security invariant. The parent contract's security relied on an internal_depositfunction to check that assets were received before minting shares. The mpETH contract overrode this internal function and moved the asset receipt check into its own publicdepositfunction. However, the team failed to account for the inherited publicmintfunction, which now called the new, check-less_depositfunction, allowing an attacker to mint shares for free. - References:
2025-06-02 - 1
- Date: 2025-06-02
- Project: #FPC
- Value Lost: $4,700,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 3.3.2: Fee-on-Transfer & Rebase Accounting Issues
- Broader Classification:
- Description: The protocol was exploited through a price manipulation attack that capitalized on the token's non-standard burn-on-transfer mechanism. The FPC token was designed to burn a portion of its own tokens directly from the liquidity pool during every sell transaction. An attacker used a flash loan to execute a large buy, drastically inflating the token's price, and then immediately sold the tokens. The flawed burn logic, combined with the artificially high price, allowed the attacker to drain the pool's liquidity.
- References:
2025-05-28 - 4
- Date: 2025-05-28
- Project: Cork Protocol
- Value Lost: ~$13,200,000 (3,761 wstETH)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- The protocol was drained via a highly sophisticated, two-vector exploit targeting complex interactions between its market automation and a custom Uniswap V4 hook.
- 1. Price Manipulation (Setup): The attacker first exploited the market's rollover pricing logic. By executing a single trade in a low-volume period just before market expiry, they skewed the volume-weighted price calculation. This allowed them to purchase a massive number of
Cover Tokensfor a near-zero cost after the rollover completed. - 2. Arbitrary Call via Malicious Hook (Drain): The primary vulnerability was an access control flaw in Cork's hook integration. The attacker deployed their own malicious contract that also acted as a Uniswap hook. This malicious hook was able to interact with Cork's hook in a way that bypassed authorization checks, which were absent because Cork had integrated an older version of a Uniswap periphery contract before an explicit authorization feature was added upstream. This bypass allowed the attacker to illegitimately withdraw
Depeg Swaps. - With both the cheaply acquired
Cover Tokensand the stolenDepeg Swaps, the attacker was able to drain the Liquidity Vault of its assets.
- References:
2025-05-23 - 3
- Date: 2025-05-23
- Project: Mango Markets Exploiter Trial
- Value Lost: $0 (Legal Precedent established, related to a $110M exploit)
- Chain: N/A (Legal/Off-Chain)
- BWC:
- Broader Classification:
BWC 11: Privacy & Regulatory Attack Vectors - Primary Classification:
BWC 11.2.3: "Code is Law" Defense Exploitation
- Broader Classification:
- Description: In a landmark ruling, U.S. District Judge Arun Subramanian vacated the fraud and manipulation convictions of Avraham Eisenberg. The judge determined that the evidence was insufficient to prove Eisenberg made "false representations" to Mango Markets, reasoning that as a decentralized, permissionless smart contract, the protocol could not be deceived. This decision validated the "code is law" defense in a US court, highlighting a critical regulatory vulnerability.
- References:
2025-05-18 - 2
- Date: 2025-05-18
- Project: KRC/BUSD AMM Pool
- Value Lost: Not Specified
- Chain: BSC
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.3.2: Fee-on-Transfer & Rebase Accounting Issues - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description: The KRC/BUSD AMM pool was drained by exploiting a deflationary (fee-on-transfer) mechanism in the KRC token. The token's contract burned 9% of the transfer amount from the recipient's balance if the recipient was the AMM pool. This burn was invisible to the AMM's accounting, causing a desynchronization where the pool's actual KRC balance became lower than its tracked reserves. The attacker repeatedly triggered this burn, manipulating the internal price before executing a final swap to drain the remaining BUSD.
- References:
2025-05-11 - 1
- Date: 2025-05-11
- Project: MBU Token
- Value Lost: $2,000,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.5: Inconsistent Scaling Bugs
- Broader Classification:
- Description: The MBU token contract was exploited due to an inconsistent scaling bug in its
depositfunction. The contract failed to properly normalize the decimal precision of different tokens when performing calculations. This allowed an attacker to deposit a small amount of BNB and receive a vastly disproportionate number of MBU tokens in return, which were then swapped for a profit of $2 million. - References:
2025-04-24 - 1
- Date: 2025-04-24
- Project: Zora Airdrop / 0x
- Value Lost: $128,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description: Zora's airdrop process allocated claimable $ZORA tokens to the 0x Settler contract, a permissionless contract designed to execute arbitrary transactions. An attacker exploited this by calling the Settler contract and instructing it to claim the tokens and send them to the attacker's own address. The root cause was the allocation of a claim (an unsafe approval) to a contract that was not designed to securely hold assets on its own behalf.
- References:
2025-03-25 - 2
- Date: 2025-03-25
- Project: Magic Internet Money (@MIM_Spell)
- Value Lost: ~$12,900,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description: The vulnerability was in the integration between the
CauldronV4andRouterOrdercontracts. When an attacker's position was liquidated, the collateral held within theRouterOrderwas correctly transferred to the liquidator. However, theRouterOrdercontract failed to update its internal state variable (inputAmount) that tracked this collateral. This created an inconsistent state where theCauldroncontract's solvency check still considered the liquidated assets as valid collateral, allowing the attacker to borrow against this "phantom collateral." - References:
2025-03-05 - 1
- Date: 2025-03-05
- Project: 1inch (Fusion V1)
- Value Lost: ~$10,000,000 (Majority returned for a bounty)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.2: Unsafe Storage & Memory Handling - Secondary Classification:
BWC 6.1: Integer Overflow & Underflow
- Broader Classification:
- Description:
- The exploit targeted a critical calldata corruption vulnerability in the deprecated 1inch Settlement (Fusion V1) contract, which was written in low-level Yul.
- The core of the vulnerability was an integer underflow in an assembly block that calculated a memory offset. By providing a crafted, extremely large
interactionLengthvalue in the order data, an attacker could cause the offset calculation to underflow. - This allowed the attacker to overwrite a different, controlled part of the calldata being assembled in memory. Specifically, they overwrote the legitimate
resolveraddress in the order's suffix data with the victim's address (a market maker). - This tricked the Settlement contract into making a privileged callback to the victim's contract, triggering a function that drained the market maker's funds. The majority of funds were later returned by the attacker in exchange for a bounty.
- References:
2025-02-23 - 1
- Date: 2025-02-23
- Project: ZeroLend
- Value Lost: ~$371,000 (Initial Exploit) + Undetermined ongoing extraction from new depositors
- Chain: Base
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 1.1.7: User Disempowerment& Extractive Design ("Zombie Market" / Cover-up)
- Broader Classification:
- Description:
- Note: This incident occurred in 2025 but was publicly exposed by Rekt.news in Jan 2026 after a 10-month cover-up.
- ZeroLend was drained of ~$371k on this date, but the team maintained a "Zombie Market" for months, attributing withdrawal failures to "high utilization" or UI bugs while keeping the deposit function active.
- Vulnerability: The attacker utilized PT-LBTC (a Pendle Principal Token) as collateral. By manipulating the price of this illiquid derivative on the lending market, the attacker was able to borrow ~3.92 real LBTC against it, effectively draining the pool. This attack vector was identical to the Ionic Money exploit that occurred just 18 days prior (Feb 4, 2025).
- Cover-up & Ongoing Extraction: ZeroLend did not disclose the loss. On-chain analysis revealed that a Gnosis Safe (created two months post-exploit) utilizing Gelato automation has been systematically withdrawing liquidity provided by new, unsuspecting depositors, effectively turning the broken protocol into a trap for users.
- Status (as of Jan 2026): The ZERO token has been delisted from major exchanges, GitHub activity has ceased, and the protocol remains largely abandoned by developers despite the frontend remaining accessible.
- References:
2025-02-03 - 2
- Date: 2025-02-03
- Project: Bybit (Centralized Exchange)
- Value Lost: ~$1,400,000,000 (401,347 ETH)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.4.4: Supply Chain Attacks (Compromised Dev Machine) - Secondary Classification:
BWC 1.3.3: Front-End Hijack/Spoofing (UI Manipulation)
- Broader Classification:
- Description:
- Bybit suffered a massive $1.4B theft from its cold wallet due to a sophisticated supply chain attack targeting its multi-signature setup.
- Vulnerability: The attack did not exploit the smart contracts directly but rather the Safe Wallet user interface via a supply chain compromise. A developer's machine was compromised, allowing attackers to inject malicious JavaScript into the Safe UI build.
- Attack Flow:
- Injection: Malicious JS was injected into the Safe UI via a compromised dev machine.
- Deception: When signers attempted routine internal transfers, the script intercepted the request. It silently replaced the transaction parameters with attacker-controlled data (redirecting the proxy implementation).
- Blind Signing: The script sent the malicious payload to the hardware wallet for signing. Crucially, the signers failed to verify the raw data on the hardware device screen against the intended transaction.
- Execution: The valid signatures were used to upgrade the wallet's implementation to a malicious contract, allowing the attacker to drain 401,347 ETH.
- Key Lesson: Multi-signature owners must verify hardware wallet prompts against the intended transaction structure (verify what you sign).
- References:
2025-01-13 - 1
- Date: 2025-01-13
- Project: UniLend
- Value Lost: ~$197,000
- Chain: EVM
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description: The attacker exploited a critical flaw in the
redeemUnderlyingfunction's health factor calculation due to an incorrect order of operations. When a user redeemed assets, the contract would first burn their LP shares and then perform the health check. However, the check incorrectly used the contract's current, pre-withdrawal token balance (which was still high) against the user's new, post-burn share balance (which was low). This mismatch led to a massively inflated health factor calculation, allowing an undercollateralized position to appear safe and enabling the attacker to drain funds. - References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2024 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2024-11-10 - 3
- Date: 2024-11-10
- Project: BGM Token
- Value Lost: Unknown (Liquidity Pool Drained)
- Chain: BSC
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures - Secondary Classification:
BWC 1.3.8: Sybil Attacks,BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description: The BGM token was exploited due to a flawed "transfer reward" mechanism. The protocol rewarded users for every transfer, allocating claims to the sender, recipient, and referrers, funded by the project's liquidity pool. An attacker exploited this by conducting a Sybil attack, creating numerous accounts and executing artificial transfers between them to farm rewards. After inflating their BGM holdings, the attacker withdrew the rewards and sold them into the pool, draining the USDT liquidity.
- References:
2024-11-24 - 2
- Date: 2024-11-24 (Disclosure Date)
- Project: Zyfy (PermissionlessPaymaster)
- Value Lost: $0 (Vulnerability Disclosure)
- Chain: zkSync
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment - Secondary Classification:
BWC 5.1.2: Back-Running
- Broader Classification:
- Description:
- A vulnerability was identified in Zyfy's Paymaster contract on zkSync regarding gas refund accounting.
- The Mechanism: On zkSync, unused gas is refunded to the paymaster. The contract tracked the intended recipient of this pending refund in a state variable called
previousManager. - The Flaw: The
selfRevokeSignerfunction allowed a user to updatepreviousManagerimmediately without checking if a refund was pending for a different manager. - The Exploit: An attacker could back-run a transaction sponsored by a legitimate manager. By calling
selfRevokeSignerimmediately after the sponsored transaction (but before the refund logic was finalized byupdateRefundin the next interaction), the attacker overwrotepreviousManagerwith their own address. Consequently, the gas refund generated by the legitimate manager's transaction was incorrectly credited to the attacker.
- References:
2024-11-16 - 1
- Date: 2024-11-16
- Project: Polter Finance
- Value Lost: ~$8,700,000
- Chain: Fantom
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.2.2: Oracle Manipulation - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- Polter Finance suffered a classic oracle manipulation attack due to its reliance on spot prices for asset valuation.
- The Flaw: The protocol determined the price of BOO tokens by averaging the spot prices from SpookySwap V2 and V3 pools. It lacked robust mechanisms like Time-Weighted Average Price (TWAP) or external Chainlink feeds for validation.
- The Exploit: An attacker used flash loans to massively skew the reserves in the underlying SpookySwap pools, artificially inflating the spot price of BOO. Because Polter's oracle blindly accepted this manipulated data, the system valued the attacker's small BOO deposit at an astronomical rate. This allowed the attacker to borrow effectively all assets held by the protocol against this inflated collateral.
- References:
2024-10-24 - 6
- Date: 2024-10-24
- Project: Ramses Exchange
- Value Lost: ~$93,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures - Secondary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description:
- Ramses Exchange was exploited due to multiple failures in its reward distribution logic for veNFTs.
- State Adjustment Failure: The protocol failed to decrease the
tokenTotalSupplyByPeriodvariable when rewards were claimed. This allowed the attacker to claim rewards without reducing the tracked supply, enabling repeated claims. - Token ID Manipulation: The attacker bypassed claim limits by minting new veNFTs with new Token IDs, effectively resetting their claim status while using the same underlying capital.
- Missing Validation: The
getPeriodRewardfunction failed to validate that the requested reward period matched the current block timestamp, allowing the attacker to claim rewards for past periods.
- References:
2024-10-28 - 5
- Date: 2024-10-28 (Audit Disclosure)
- Project: Royco Protocol
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum, Arbitrum, Base
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.8: Faulty Array & List Handling
- Broader Classification:
- Description:
- A critical vulnerability was identified in the Royco Protocol's
RecipeKernelduring a security review. - The Flaw: The protocol allowed Incentive Providers (IPs) to create offers with an array of reward tokens (
incentivesOffered). However, the system failed to sanitize this array for duplicate token addresses. - The Exploit: An attacker could create an offer where the same reward token was listed multiple times (e.g.,
[USDC, USDC]). When an Action Provider (AP) filled the offer, the contract iterated through this array to distribute rewards. Because the tracking mechanism (incentiveAmountsOffered) summed the total rewards correctly but the distribution loop iterated over the duplicate keys, the system would pay out the full reward amount for each occurrence of the token in the array. This resulted in the AP receiving multiples of the intended reward (e.g., double the amount if listed twice), allowing them to drain funds from the kernel.
- A critical vulnerability was identified in the Royco Protocol's
- References:
2024-10-31 - 4
- Date: 2024-10-31 (Disclosure Date)
- Project: DeFi Wonderland (opUSDC Bridge)
- Value Lost: $0 (Vulnerability Disclosure)
- Chain: OP Stack Chains
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.8: DoS in Cross-Chain Messaging Protocols - Secondary Classification:
BWC 10.4: Protocol Upgrade-Induced Vulnerabilities
- Broader Classification:
- Description:
- A critical DoS vulnerability was identified in the opUSDC bridging standard, specifically regarding the migration path from "Bridged USDC" to "Native USDC."
- The Mechanism: Bridging involves locking USDC on L1 and minting it on L2. If the L2 mint fails (e.g., Out Of Gas), the message is queued and can be replayed later.
- The Flaw: The protocol allows for a "Migration" event where the L2 USDC token ownership is transferred to Circle to become native. Crucially, this revokes the Bridge Adapter's permission to mint.
- The Lock: If a user has a pending/failed L2 mint transaction at the moment the migration occurs, the Bridge Adapter loses its minting rights before the user can replay the transaction. The replay will permanently revert (due to missing permissions), leaving the user's funds irretrievably locked in the L1 bridge contract.
- References:
2024-10-05 - 3
- Date: 2024-10-05
- Project: AIZPT (AIZPT314)
- Value Lost: ~$20,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.4: Calculation Errors - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- The AIZPT314 token contract was exploited due to a fundamental mathematical error in its custom trading logic.
- The Flaw: The protocol implemented a flawed pricing formula (
token0Out = token1In * token0InContract / (token1In + token1InContract)) for swapping BNB for AIZPT. This implementation effectively used a quote-like or simplified formula that did not correctly account for slippage or align with the sell-side formula (which used standard Uniswap V2 logic). - The Exploit: This discrepancy created a massive arbitrage opportunity. An attacker flashloaned BNB, bought AIZPT at the undervalued "linear" rate defined by the flawed buy formula, and then sold it back using the standard curve logic (or simply traded back and forth), extracting the contract's liquidity.
- References:
2024-10-10 - 2
- Date: 2024-10-10
- Project: HYDT
- Value Lost: ~$5,800
- Chain: BSC
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 4.2.1: Insufficient Oracle Validation
- Broader Classification:
- Description: The HYDT token system was exploited via a price manipulation attack on its
InitialMintcontract. The contract allowed users to mint HYDT tokens by depositing BNB, with the exchange rate determined directly by the WBNB/USDT spot price on PancakeSwap. An attacker utilized a flash loan to borrow USDT and buy a large amount of WBNB, drastically skewing the spot price. They then deposited BNB into theInitialMintcontract at this manipulated rate to mint an inflated amount of HYDT tokens, which were subsequently sold for a profit. - References:
2024-10-15 - 1
- Date: 2024-10-15
- Project: Uniswap V4 Core
- Value Lost: $0 (Critical Audit Finding)
- Chain: Celo (and EVM chains where Native Token = ERC20)
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.3.1: Double EntryPoint Tokens - Secondary Classification:
BWC 3.3.3: Improper Handling of Native Tokens
- Broader Classification:
- Description:
- A critical vulnerability was uncovered during the audit of Uniswap V4 involving chains where the native currency also exists as an ERC-20 token (Double EntryPoint), such as CELO on Celo.
- The Mechanism: The protocol's
settlefunction calculates debt (deltas) differently for native assets (usingmsg.value) and ERC-20 tokens (usingbalanceNow - balanceBefore). - The Exploit: An attacker could exploit this dual nature by first calling
syncto snapshot balances, then callingsettlesending native value (increasing the delta viamsg.value). Crucially, this action also increases the contract's ERC-20 balance. The attacker could then immediately callsettleagain using the token's ERC-20 address. The contract would interpret the previousmsg.valuedeposit as a new ERC-20 transfer (sincebalanceNow>balanceBefore), effectively crediting the user twice for the same funds. - Impact: This accounting flaw would allow an attacker to inflate their balance artificially and drain the pool's liquidity without transferring the corresponding assets.
- References:
2024-09-25 - 7
- Date: 2024-09-25 (Disclosure Date)
- Project: Fuel Network (Fuel VM)
- Value Lost: $0 (Critical Vulnerability Disclosure)
- Chain: Fuel
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.4.1: Incorrect VM Gas Charges - Secondary Classification:
BWC 8.4: DoS via Numeric Calculation(Resource Exhaustion)
- Broader Classification:
- Description:
- A critical vulnerability was identified in the Fuel VM's
CCP(Code Copy) instruction during the Fuel Attackathon. - The Flaw: The
CCPinstruction copies code from a contract into memory but charged gas based solely on the size of the source contract's bytecode, not the actual number of bytes copied or the memory region affected. Furthermore, if the destination memory region exceeded the source bytecode size, the instruction would zero-fill the excess area. - The Exploit: An attacker could manipulate the
offsetandlengthparameters to trigger a massive memory zero-filling operation (a resource-intensive task) while paying a negligible gas fee calculated only on the small contract size. This discrepancy allowed for "cheap" memory clearing, leading to potential network resource exhaustion and Denial of Service (DoS) attacks by underpricing computational work.
- A critical vulnerability was identified in the Fuel VM's
- References:
2024-09-10 - 6
- Date: 2024-09-10
- Project: Pythia Finance
- Value Lost: ~$53,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures - Secondary Classification:
BWC 6.4: Calculation Errors
- Broader Classification:
- Description: The Pythia Finance staking contract contained a critical logic error in its reward calculation. The formula calculated rewards by simply multiplying the user's current balance by an accumulating
rewards-per-shareglobal variable. Crucially, it failed to subtract the "debt" (rewards accumulated before the user staked), effectively acting as if the user had been staking since the protocol's inception. This allowed an attacker to deposit a large amount, immediately claim massive rewards proportional to the protocol's lifetime history, and exit. - References:
2024-09-03 - 5
- Date: 2024-09-03
- Project: Penpie
- Value Lost: ~$27,000,000
- Chain: Ethereum, Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.1.1: Standard Reentrancy - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- Penpie, a yield optimizer built on Pendle Finance, was exploited via a sophisticated reentrancy attack enabled by the permissionless registration of new markets.
- The Setup: The attacker registered a valid Pendle market but linked it to a malicious custom token (SY contract). They then triggered
batchHarvestMarketRewards. - The Reentrancy: This function calculated rewards by checking token balances before and after calling
redeemRewards. During theredeemRewardscall, the malicious token's transfer logic handed execution control back to the attacker. - The Exploit: Inside this reentrancy window, the attacker called
depositMarketto deposit a large amount of funds. This legitimate deposit increased the protocol's token balance. When the execution returned to theharvestfunction, it read the now-inflated "after" balance. The protocol incorrectly interpreted the difference (which included the attacker's deposit) as massive rewards earned, distributing them to the attacker.
- References:
2024-09-26 - 4
- Date: 2024-09-26
- Project: Onyx Protocol
- Value Lost: ~$3,800,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.2: Precision Loss & Rounding Errors - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- Onyx Protocol, a fork of Compound V2, was exploited in a repeat of the "empty market" attack.
- Precision Loss (Inflation): The protocol launched a new, low-liquidity market (VUSD) without burning initial liquidity ("dead shares"). An attacker exploited the known Compound V2 exchange rate calculation vulnerability by continuously minting and redeeming tiny amounts of shares. This process manipulated the exchange rate due to rounding errors, allowing the attacker to borrow assets worth far more than their collateral.
- Input Validation Failure: Additionally, the attacker exploited a vulnerability in Onyx's custom
NFTLiquidationcontract. The contract failed to validate input parameters during the liquidation process, allowing the attacker to use a fake token or manipulated data to self-liquidate positions and claim inflated rewards, exacerbating the loss.
- References:
2024-09-01 - 3
- Date: 2024-09-01 (Incident Month)
- Project: Maia DAO
- Value Lost: $0 (Funds Rescued / ~$1.2M At Risk)
- Chain: Arbitrum, Metis (Multichain)
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control - Secondary Classification:
BWC 3.2.7: Broken Invariant via Function Overriding
- Broader Classification:
- Description:
- A critical vulnerability was discovered in Maia DAO's
CoreBranchRoutercontract. The flaw stemmed from a failure to override avirtualfunction (callOut) in the deployed contract. The parent contract's default implementation of this function lacked the specific access controls required for the live system, as it was intended to be overridden by the child contract with proper restrictions. - The Exploit Vector: This "missing override" oversight meant the public, unsecured parent function was exposed. It would have allowed an attacker to call the function and impersonate a trusted
CoreBranchRouter, enabling them to bypass security checks and drain funds from theCoreRootRouteror brick the system. - Outcome: The vulnerability was identified by a whitehat hacker, and the Maia DAO team successfully executed a rescue operation to secure the ~$1.2M at risk before any malicious exploitation occurred.
- A critical vulnerability was discovered in Maia DAO's
- References:
2024-09-23 - 2
- Date: 2024-09-23
- Project: Bankroll Network
- Value Lost: ~$235,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.1.1: Insufficient Input Validation - Secondary Classification:
BWC 6.1: Integer Overflow & Underflow
- Broader Classification:
- Description: The
BankrollNetworkStackcontract was exploited due to a critical input validation failure in thebuyForfunction. The function allowed users to purchase shares on behalf of another address (_customerAddress) but failed to validate that this address was not the vault contract itself. An attacker exploited this by repeatedly callingbuyForwith the vault's address as the customer, using the vault's own balance to simulate "buys". This artificially inflated theprofitPerShareand the dividends attributed to the attacker (via the "divs" mechanism), allowing them to withdraw an inflated amount of WBNB, draining the pool. - References:
2024-09-27 - 1
- Date: 2024-09-27
- Project: Bedrock (uniBTC)
- Value Lost: ~$1,700,000
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.3.3: Improper Handling of Native Tokens - Secondary Classification:
BWC 3.2.2: Faulty Contract Checks
- Broader Classification:
- Description:
- The Bedrock protocol was exploited due to a critical flaw in how it handled native tokens on non-Bitcoin chains (e.g., ETH on Ethereum).
- The Mechanism: The system allowed minting
uniBTCat a 1:1 ratio against BTC-equivalent assets. To prevent minting against non-equivalent assets (like ETH), the protocol set acapof 0 for those assets. - The Flaw: The
totalSupplyfunction, used to enforce this cap, mistakenly returned0for theNATIVE_BTCaddress because the native token was not properly registered in theSigmaSuppliercontract. - The Exploit: This logic error meant the check
totalSupply <= capevaluated to0 <= 0(True), bypassing the restriction. An attacker was able to deposit ETH (valued much lower than BTC) and mintuniBTCat a 1:1 ratio, effectively buying Bitcoin for the price of Ether and draining the protocol's liquidity.
- References:
2024-08-06 - 6
- Date: 2024-08-06
- Project: Ronin Bridge
- Value Lost: ~$12,000,000 (Returned by Whitehats)
- Chain: Ethereum / Ronin
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.1: Improper Initialization - Secondary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description:
- The Ronin Bridge was exploited due to a critical initialization failure during a contract upgrade.
- The Flaw: The development team upgraded the bridge proxy from version 2 to version 4 but neglected to call the intermediate
initializeV3function. This function was responsible for initializing the_totalOperatorWeightvariable. - The Impact: Because the initialization was skipped,
_totalOperatorWeightdefaulted to0. The bridge's logic checked if the weight of provided signatures met the threshold derived from this variable. With the threshold effectively set to zero, the contract accepted empty or invalid signatures as valid authorization for withdrawals. This allowed an MEV bot (acting as a whitehat) to front-run an attack and withdraw ~$12M in ETH and USDC, effectively bypassing the bridge's multi-signature security.
- References:
2024-08-13 - 5
- Date: 2024-08-13
- Project: VOW
- Value Lost: ~$1,200,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment - Secondary Classification:
BWC 5.1.2: Back-Running
- Broader Classification:
- Description:
- The VOW token was exploited due to a critical operational security failure involving non-atomic testing in production.
- The Flaw: The development team attempted to test a configuration change by sending a transaction to modify a critical parameter (setting the
usdvariable to thevowtoken address) with the intention of reverting it in a subsequent transaction. This created a temporal gap where the contract was live on mainnet in an invalid, vulnerable state. - The Exploit: An attacker monitored the mempool, observed the configuration change, and back-ran the transaction. Within the window before the team could revert the change, the attacker exploited the "abnormal" state—where the system treated VOW as the stable peg—to mint 100 million vUSD tokens, which were then dumped for profit.
- References:
2024-08-30 - 4
- Date: 2024-08-30 (Audit Disclosure)
- Project: Uniswap V4 Periphery
- Value Lost: $0 (Critical Audit Finding)
- Chain: EVM (Uniswap V4)
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.11: DoS via Front-Running (Griefing) - Secondary Classification:
BWC 5.1.1: Front-Running
- Broader Classification:
- Description:
- A Denial of Service vulnerability was identified in the Uniswap V4 Periphery contracts regarding the integration of Permit2 within multicalls.
- The Flaw: The contracts allowed users to bundle a Permit2 signature approval (
permit) alongside other actions (likeaddLiquidityorswap) in a singlemulticalltransaction. The code expected thepermitcall to execute successfully. - The Exploit: An attacker could observe the pending
multicalltransaction, extract the valid Permit2 signature, and front-run the transaction by submitting the signature directly to the Permit2 contract. This consumes the signature's nonce. When the user'smulticalltransaction attempts to execute thepermit, it reverts because the nonce has already been used. Since themulticallrelies on all sub-calls succeeding, the entire transaction (including the intended swap or deposit) fails.
- References:
2024-08-29 - 3
- Date: 2024-08-29 (Disclosure Date)
- Project: Alchemix Finance
- Value Lost: $0 (Critical Vulnerability Disclosure)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.8: Faulty Array & List Handling
- Broader Classification:
- Description:
- A critical vulnerability was identified in Alchemix's
VotingEscrowcontract regarding how it handled historical data lookups. - The Flaw: The protocol used a binary search algorithm to retrieve historical voting power or supply from a
pointHistoryarray based on timestamps. However, the system allowed multiple checkpoints to be created with the exact same timestamp (e.g., within the same block). The binary search implementation was not designed to handle these duplicate keys; it would stop at the first match it found rather than the latest (right-most) entry. - The Exploit: An attacker could strategically create multiple checkpoints at a specific timestamp to insert duplicate entries. By manipulating which entry the binary search returned (due to its non-deterministic handling of duplicates), the attacker could force the contract to use stale or manipulated data, potentially inflating their voting power or influencing governance outcomes.
- A critical vulnerability was identified in Alchemix's
- References:
2024-08-30 - 2
- Date: 2024-08-30 (Audit Disclosure)
- Project: Superposition AMM
- Value Lost: $0 (Critical Audit Finding)
- Chain: Superposition (EVM)
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.3.5: EIP Standard Non-Compliance - Secondary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description:
- A critical vulnerability was identified in the
OwnershipNFTs.solcontract during an audit. - The Flaw: The contract implemented a custom version of the ERC-721 standard but failed to adhere to a specific requirement: clearing the
getApprovedaddress (token level approval) upon a token transfer. - The Exploit: An attacker (Token Owner) could approve the NFT to a secondary address they control, sell the NFT to a victim, and then—because the approval was not revoked during the transfer—use the secondary address to call
transferFromand steal the NFT back from the buyer immediately.
- A critical vulnerability was identified in the
- References:
2024-08-30 - 1
- Date: 2024-08-30 (Audit Disclosure)
- Project: Uniswap V4 Periphery
- Value Lost: $0 (Critical Audit Finding)
- Chain: EVM (Uniswap V4)
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.3: Unsafe Type Casting - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- A high-severity vulnerability was identified in the Uniswap V4 Periphery during an audit. The flaw existed in the
validateMinOutfunction, which is responsible for enforcing slippage protection. - The Flaw: The function performed an unsafe cast from
int128(liquidity delta) touint128. In Uniswap V4, hooks can return a negativeliquidityDelta. When a negative value is cast directly to an unsigned integer, it underflows and wraps around to a massive positive number (e.g., casting-1results in2^128 - 1). - The Exploit: An attacker could exploit this by interacting with a hook that returns a negative delta. The unsafe cast would incorrectly interpret this as a massive liquidity increase, bypassing the minimum output check (slippage protection) because the system would believe the user received a huge amount of assets.
- Mitigation: The issue was resolved by using
SafeCast.toUint128, which correctly reverts if the value is negative.
- A high-severity vulnerability was identified in the Uniswap V4 Periphery during an audit. The flaw existed in the
- References:
2024-07-23 - 2
- Date: 2024-07-23
- Project: Delta Prime
- Value Lost: ~$1,000,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.2.1: Unsafe Storage Use - Secondary Classification:
BWC 3.2.1: Improper Initialization
- Broader Classification:
- Description:
- Delta Prime was exploited due to a critical storage collision vulnerability inherent in its proxy architecture, compounded by a forgotten initialization function.
- The Architecture: The project used a
DiamondBeaconProxypattern. User "Prime Accounts" were clones that delegatecalled to aDiamondBeacon, which then delegated to implementation facets. - The Flaw: Both the Prime Account proxy and the Diamond contract utilized the same storage slot to store the
owneraddress. However, they used different storage slots to track theirinitializedstatus. Additionally, the developers failed to remove or protect theinitfunction on the DiamondBeacon after deployment. - The Exploit: An attacker invoked the
initfunction on other users' Prime Accounts. This call was delegated to the Diamond'sinitlogic. Because the Diamond checked a differentinitializedstorage slot (which was empty in the context of the Proxy), the check passed. The function then overwrote theownerstorage slot—which was shared by the Proxy—granting the attacker full control over the victims' Prime Accounts and allowing them to drain funds.
- References:
2024-07-23 - 4
- Date: 2024-07-23
- Project: Spectra Finance
- Value Lost: ~$73,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls - Secondary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description:
- Spectra Finance was exploited due to an arbitrary call vulnerability within its router's swap logic.
- The Flaw: The protocol allowed users to execute trades via KyberSwap, but failed to validate the
kyberRouteraddress and thetargetDatapayload passed to the_dispatchfunction (command type0x12). - The Exploit: An attacker exploited this by passing the
asdCRVtoken address as thekyberRouterand encoding atransferFromcall in thetargetData. Since the Spectra router executed this call as itself, and users had previously approved the Spectra router to spend theirasdCRVtokens, the attacker was able to drain funds from user wallets directly to their own.
- References:
2024-07-16 - 3
- Date: 2024-07-16
- Project: Li.Fi (Jumper Exchange)
- Value Lost: ~$11,600,000
- Chain: Ethereum, Arbitrum
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls - Secondary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description:
- The Li.Fi DEX aggregator was exploited due to a critical arbitrary call vulnerability in a newly deployed facet.
- The Flaw: The protocol introduced a feature allowing users to deposit tokens and specify a route for swapping. However, the contract failed to sanitize the
targetaddress andcallDataprovided by the user. - The Exploit: An attacker crafted a malicious route where the
targetwas a popular token contract (e.g., USDT, USDC) and thecallDatawas atransferFromcall. Since the Li.Fi contract executed this call, and many users had granted infinite approvals to the Li.Fi contract, the attacker was able to use the protocol as a "confused deputy" to drain tokens directly from users' wallets into their own.
- References:
2024-07-12 - 2
- Date: 2024-07-12
- Project: Dough Finance
- Value Lost: ~$1,800,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.3.1: Missing Validation in Callbacks - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description: The
ConnectorDeleverageParaswapcontract was exploited due to a critical validation failure in its flashloan callback execution. Users could initiate a flashloan viaflashloanReqand provide aswapDataparameter, intended to specify trade details for a ParaSwap interaction. This data was passed through to theexecuteOperationcallback. However, the callback logic (deloopAllCollaterals) failed to validate or sanitize this user-supplied data. This allowed an attacker to craft maliciousswapDatathat, instead of executing a swap, triggered a directWETH.transferFromcall, stealing assets that users had approved to the contract. - References:
2024-07-24 - 1
- Date: 2024-07-24
- Project: Compound DAO
- Value Lost: $0 (Governance Takeover Averted; ~$25M Assets at Risk)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.1: DAO Governance Attacks - Secondary Classification:
BWC 1.3.1: Social Engineering Exploits
- Broader Classification:
- Description:
- The Compound DAO faced a hostile governance takeover attempt by a group known as the "GoldenBoyz." The attack aimed to pass Proposal 289, which sought to transfer 499k COMP tokens ($25M) from the treasury to a vault, while simultaneously delegating the voting power of those tokens to the proposers.
- Governance Exploit: Given Compound's low voter turnout (4-5%), gaining control of these tokens (5% of supply) would have allowed the attackers to unilaterally dictate future governance outcomes.
- Social Engineering & Timing: The attackers used failed "test" proposals (247 and 279) to gauge community resistance. For the final malicious proposal, they employed "stealth voting," casting the majority of "for" votes at the very end of the voting window to limit the community's ability to react.
- Mitigation: The proposal passed, but the community responded with Proposal 290 to move administrative control to a Community Multisig. A truce was eventually reached, and the immediate threat to the protocol's governance was neutralized.
- References:
- OpenZeppelin Analysis (Contextual Link based on description)
2024-06-25 - 1
- Date: 2024-06-25 (Audit Disclosure)
- Project: Taiko (Bridge)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Taiko / Ethereum
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.5.1: Parser Differential / Inconsistent Validation - Secondary Classification:
BWC 2.2.4: Composable Arbitrary Calls
- Broader Classification:
- Description:
- A critical vulnerability was discovered in Taiko's bridge message processing logic during an audit, exemplifying a Parser Differential bug.
- The Mechanism: The bridge handled cross-chain messages via two distinct paths:
processMessage(immediate execution) andretryMessage(delayed execution for rate-limited messages). - The Flaw: The immediate execution path correctly validated inputs to prevent calls to forbidden addresses. However, the
retryMessagepath inconsistently applied these validations, skipping the forbidden address check entirely. - The Exploit: An attacker could intentionally trigger the rate limit to force a malicious message into the "Retriable" state. They could then execute the message via the vulnerable
retryMessagepath, bypassing the security checks. This would allow them to execute arbitrary calls (liketransferFrom) against forbidden targets (like token contracts) with the Bridge acting asmsg.sender.
- References:
2024-06-10 - 5
- Date: 2024-06-10
- Project: UWU Lend
- Value Lost: ~$19,300,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 5.2.4: Over-Leverage & Liquidation Spirals
- Broader Classification:
- Description:
- UWU Lend was exploited due to a combination of fragile economic parameters and oracle manipulation.
- The Flaw (Over-Leverage): The protocol configured the sUSDE market with a Liquidation Threshold of 90% and a Liquidation Bonus of 10%. This left effectively zero margin for error (90% + 10% = 100%).
- The Exploit (Price Manipulation): An attacker manipulated the price of the collateral asset (sUSDE) down by just ~4% using a flash loan and curve pool imbalances. Because of the aggressive LTV parameters, this minor fluctuation allowed the attacker to liquidate their own position profitably. They could borrow assets, trigger the liquidation, and receive the 10% bonus which, combined with the manipulated price, exceeded the debt repayment cost, draining the protocol.
- References:
2024-06-19 - 4
- Date: 2024-06-19 (Audit Disclosure)
- Project: Linea (PLONK Go Prover)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Linea (Layer 2)
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.3.4: Forgetting to Blind Polynomials in ZK Protocols
- Broader Classification:
- Description:
- A critical cryptographic vulnerability was identified in Linea's PLONK Go Prover implementation during a security audit.
- The Theory: In ZK-SNARKs, provers generate polynomials to represent secret data (the witness). To prevent the verifier from reconstructing these polynomials (and thus learning the secret) via the revealed evaluations, the polynomials must be "blinded" by adding random coefficients.
- The Flaw: The Linea implementation split the quotient polynomial into "shards" but failed to apply blinding to these individual shards.
- The Impact: Without this blinding, the evaluations provided during the proof generation process leaked excessive information. This could allow an attacker to statistically reconstruct the polynomial and recover the secret witness, completely compromising the zero-knowledge property of the system.
- References:
2024-06-11 - 3
- Date: 2024-06-11 (Audit Disclosure)
- Project: Opal Protocol (Omnipool)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.3.1: Lack of Slippage Control - Secondary Classification:
BWC 5.1.3: Sandwich Attacks
- Broader Classification:
- Description:
- A critical vulnerability was identified in the Opal Omnipool's reward claiming logic during a security review.
- The Flaw: When users claimed rewards, the contract executed a
Balancer.batchSwapto convert tokens. However, the function call failed to specify a minimum output amount (limits), effectively accepting 100% slippage. - The Exploit: An attacker could exploit this by monitoring the mempool for reward claim transactions. They could "sandwich" the transaction by front-running it to manipulate the pool's price and back-running it to capture the slippage. This would allow the attacker to siphon off a significant portion, if not all, of the user's rewards.
- References:
2024-06-20 - 2
- Date: 2024-06-20 (Audit Disclosure)
- Project: Boost AA Wallet
- Value Lost: $0 (Critical Audit Finding)
- Chain: EVM (Optimism, Base, etc.)
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.3.1: Weak Random Number Generation - Secondary Classification:
BWC 1.4.1: Compromised Validator/Node(Context: Validator manipulation)
- Broader Classification:
- Description:
- A critical vulnerability was identified in the Boost AA Wallet's raffle mechanism during an audit.
- The Flaw: The protocol determined raffle winners using
block.prevrandaoandblock.timestampas the sole sources of randomness. - The Exploit: While these values are hard for a regular user to predict in advance, a malicious validator (or a sequencer in L2 contexts) has control over block production. They could simulate the raffle result for a pending block and choose to withhold the block or reorganize transactions if the outcome is not favorable, effectively "re-rolling" the dice until they win.
- References:
2024-06-14 - 1
- Date: 2024-06-14 (Public Disclosure)
- Project: Alchemix
- Value Lost: $0 (Bounty Paid: ~$28,730)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control - Secondary Classification:
BWC 5.1.3: Sandwich Attacks
- Broader Classification:
- Description: A high-severity vulnerability was identified in Alchemix's yield harvesting logic involving its integration with Gelato. The protocol intended to mitigate sandwich attacks during yield unwrapping by restricting the
harvestfunction—which accepts aminimumAmountOutparameter—to be callable only by the Gelato Automate contract. However, Alchemix integrated the generic, public Gelato Automate contract rather than a dedicated proxy. Because the generic contract allows any user to schedule tasks, an attacker could have scheduled a task instructing Gelato to callharvestwithminimumAmountOutset to zero. This would satisfy themsg.sendercheck (as the call comes from Gelato) while allowing the attacker to sandwich the transaction and steal the harvested yield. - References:
2024-05-20 - 7
- Date: 2024-05-20 (Audit Disclosure)
- Project: Elfi Protocol
- Value Lost: $0 (Critical Audit Finding)
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.4.2: Flawed Incentive Structures - Secondary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description:
- A critical vulnerability was identified in the Elfi Protocol's staking mechanism during a Sherlock audit.
- The Flaw: The protocol issued transferable
stakeToken(st) as proof of deposit but calculated rewards based on the account's currentstbalance rather than an internal, non-transferable staking record. - The Exploit: This created a "double-dipping" vulnerability. An attacker could stake tokens in Account A, transfer the
sttokens to Account B, and claim rewards on Account B. They could then transfer thesttokens back to Account A (or to Account C) and claim rewards again for the same time period, effectively multiplying the yield generated by a single deposit.
- References:
2024-05-27 - 6
- Date: 2024-05-27
- Project: RedKeysGame
- Value Lost: ~$10,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.3.1: Weak Random Number Generation
- Broader Classification:
- Description: The
RedKeysGamecontract was exploited due to a Weak RNG vulnerability. The contract determined the winner of a betting game by deriving a "random" number from predictable on-chain variables, including the block'stimestamp,prevrandao(difficulty),gaslimit,coinbase, andnumber. An attacker deployed a malicious contract that pre-calculated the result using these same publicly available values before submitting the bet in the same transaction block. This allowed the attacker to guarantee a win every time, draining the contract's funds. - References:
2024-05-16 - 5
- Date: 2024-05-16
- Project: TCH Token
- Value Lost: ~$18,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 7: Low-Level & EVM-Specific Vulnerabilities - Primary Classification:
BWC 7.3.2: Malleable ecrecover - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- The TCH token contract was exploited due to a "CTF-style" signature malleability vulnerability.
- The Flaw: The
burnTokenfunction usedecrecoverto validate signatures from an authorized signer. Crucially, the replay protection mechanism tracked the uniqueness of the signature bytes rather than the message digest or a nonce. - The Exploit: An attacker harvested valid, previously used signatures and modified the
vvalue (e.g., from0x01to0x1c). Due to the malleability of ECDSA signatures in Ethereum (wheresand-smodnare both valid),ecrecoverresolved this modified signature to the same authorized signer. However, because the signature bytes were technically different, it bypassed the contract's "already used" check. - The Impact: The attacker replayed these burn authorizations to burn a significant amount of TCH tokens held by the PancakeSwap liquidity pair. This artificially inflated the token price, allowing the attacker to sell their holdings for a profit.
- References:
2024-05-28 - 4
- Date: 2024-05-28 (Audit Disclosure)
- Project: Scroll (Batch Token Bridge)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.1.2: ERC-777 Reentrancy - Secondary Classification:
BWC 3.2.1: Improper Initialization(Related to configuration, but not the primary exploit)
- Broader Classification:
- Description:
- A critical reentrancy vulnerability was identified in the Scroll Batch Token Bridge during an audit.
- The Flaw: The
depositERC20function initiated a token transfer usingsafeTransferFrombefore calling the internal_depositfunction. Crucially, thenonReentrantmodifier was placed on the internal_depositfunction rather than the externaldepositERC20entry point. - The Exploit: An attacker using a token with sender hooks (such as ERC-777 or compliant ERC-20s with callbacks) could re-enter the
depositERC20function during thesafeTransferFromcall. Because the execution flow had not yet reached the_depositfunction where the guard resided, the reentrancy check was bypassed. This allowed the attacker to stack multiple deposits in a single transaction, potentially inflating their credited amount on L2 or locking funds in the bridge.
- References:
2024-05-29 - 3
- Date: 2024-05-29
- Project: Scroll Token (Custom Token on Scroll L2)
- Value Lost: Token Price Plunged ~99% (Amount Unknown)
- Chain: Scroll
- BWC:
- Broader Classification:
BWC 6: Arithmetic & Numeric Vulnerabilities - Primary Classification:
BWC 6.1: Integer Overflow & Underflow
- Broader Classification:
- Description: The "Scroll Token" (a custom ERC-20 token deployed on the Scroll network, not the network's native token) was exploited due to a classic integer underflow. The developers placed a subtraction operation within an
uncheckedblock to optimize gas, assuming the "from" balance was sufficient. However, the logic allowed a transfer from an address with a zero balance to underflow, wrapping around to the maximumuint256value. This allowed the attacker to mint a massive amount of tokens and dump them, crashing the price. - References:
2024-05-10 - 2
- Date: 2024-05-10
- Project: Galaxy Fox
- Value Lost: ~$330,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description: The Galaxy Fox token contract was exploited due to a critical access control failure in its airdrop logic. The protocol used a Merkle Tree to distribute tokens, but the
setMerkleRootfunction—intended for admin use to update the eligible claim list—was left public with no authorization checks. An attacker called this function to overwrite the legitimate root with a malicious one, for which they possessed a valid leaf path. This allowed them to fraudulently claim a massive amount of GFOX tokens, which they immediately swapped for ETH in the Uniswap pool. - References:
2024-05-10 - 1
- Date: 2024-05-10
- Project: TSURU
- Value Lost: ~$410,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.3.1: Missing Validation in Callbacks
- Broader Classification:
- Description: The TSURUWrapper contract was exploited due to a critical validation failure in its
onERC1155Receivedhook. This function is a standard callback intended to be triggered only by theTSURUtoken contract upon a safe transfer. However, the function lacked a check to verify thatmsg.senderwas the actual token contract. This allowed an attacker to call the hook directly, spoofing a deposit and minting unlimited tokens to themselves, which were then used to drain the Uniswap pool. - References:
2024-04-25 - 1
- Date: 2024-04-25
- Project: NGFS Token
- Value Lost: ~$190,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.1: Improper Initialization - Secondary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description:
- The NGFS token contract was exploited due to a failure to properly lock critical configuration variables upon deployment.
- The Flaw: The contract included a
uniswapV2Deleflag intended to lock the privileged_uniswapV2Proxyaddress after initialization. However, the deployer failed to set this flag totrueduring the deployment process. - The Exploit: Because the lock was open, an attacker was able to call the initialization function (or a setter protected by this flag) to overwrite the
_uniswapV2Proxywith their own address. This granted them privileged access to restricted operations, allowing them to mint unlimited tokens and drain the liquidity pool.
- References:
2024-04-08 - 9
- Date: 2024-04-08
- Project: Squid Game (SQUID)
- Value Lost: ~$87,000
- Chain: BSC
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.3.1: Lack of Slippage Control - Secondary Classification:
BWC 2.1.1: Missing Access Control,BWC 5.1.3: Sandwich Attacks
- Broader Classification:
- Description:
- The
SquidTokenSwapcontract was exploited due to a combination of insufficient slippage protection and missing access control on a critical function. - The Flaw: The contract exposed a public function (
sellSwappedTokens) that allowed any user to trigger a swap of tokens held by the contract on PancakeSwap. Crucially, this function enforced a hardcoded slippage tolerance of 5%, which is excessively wide for an automated, public function. - The Exploit: An attacker utilized a sandwich attack strategy. They first front-ran the swap to push the price to the limit of the 5% tolerance. Then, they triggered the contract's swap function (which executed at the manipulated bad price). Finally, they back-ran the transaction to sell and capture the profit from the price movement, draining value from the protocol.
- The
- References:
2024-04-01 - 8
- Date: 2024-04 (Incident Month)
- Project: Hackathon Token
- Value Lost: Unknown
- Chain: BSC
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.4: Self Transfers and Transaction Timing Attacks - Secondary Classification:
BWC 6.4: Calculation Errors
- Broader Classification:
- Description:
- The Hackathon token was exploited due to a flawed custom transfer logic that failed to handle self-transfers correctly, specifically when an AMM pair was both the sender and recipient.
- The Flaw: The token's transfer function contained logic intended to manage reserves but did not validate if
from == to. When tokens were sent to the pair address, the faulty accounting logic effectively doubled the balance of the pair instead of netting it out. - The Exploit: An attacker sent excess tokens to the Uniswap-like pair and called the
skimfunction (which syncs balances to reserves) with the pair itself as the destination. The self-transfer bug doubled the "excess" tokens in the pair's balance. The attacker then calledskimagain, this time to their own address, to extract the artificially created surplus.
- References:
2024-04-19 - 7
- Date: 2024-04-19
- Project: Hedgey Finance
- Value Lost: ~$44,700,000
- Chain: Ethereum, Arbitrum
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.1: Unsafe Token Approvals - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- Hedgey Finance was exploited due to a critical "lingering approval" vulnerability combined with insufficient input validation.
- The Flaw: The
createLockedCampaignfunction allowed users to specify aclaimLockupstruct, which included atokenLockeraddress. The contract would automatically approve thistokenLockeraddress to spend the campaign's tokens. Crucially, the protocol failed to validate that thetokenLockerwas a trusted Hedgey contract. Furthermore, when a campaign was canceled, the protocol returned the funds but failed to revoke (reset to zero) the token allowance granted to thetokenLocker. - The Exploit: An attacker created a campaign using a malicious contract address as the
tokenLocker. This tricked the Hedgey contract into approving the attacker's contract to spend its funds. The attacker then canceled the campaign to retrieve their initial deposit. Because the approval was not revoked, the attacker's malicious contract retained the ability to spend funds from the Hedgey contract, which they then used to drain approximately $44.7M in assets.
- References:
2024-04-30 - 6
- Date: 2024-04-30 (Audit Disclosure)
- Project: Renzo Finance
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.1: DoS via External Calls
- Broader Classification:
- Description:
- A critical Denial of Service vulnerability was identified in Renzo Finance's withdrawal logic during an audit.
- The Flaw: The protocol used the legacy Solidity function
.transfer()to send ETH to users withdrawing their assets. This function enforces a hardcoded gas limit of 2300 gas on the recipient's execution. - The Impact: This gas stipend is insufficient for many smart contract wallets (e.g., Gnosis Safe, Argent, or wallets with complex
receivelogic) to process the incoming transaction. Consequently, legitimate withdrawals to these addresses would strictly fail with an "Out of Gas" error, effectively locking the users' funds in the contract with no way to claim them.
- References:
2024-04-16 - 5
- Date: 2024-04-16 (Audit Disclosure)
- Project: Mantle Network (CrossDomainMessenger)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Mantle
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description:
- A critical vulnerability was identified in Mantle's
CrossDomainMessengercontract during an audit. This contract is responsible for bridging assets and relaying messages between L1 and L2. - The Mechanism: When bridging tokens, they are minted to the
CrossDomainMessengeron the destination chain. The messenger then callsrelayMessageto execute the user's cross-chain intent. If a call fails, the funds remain in the messenger contract, waiting for a replay. - The Flaw: The
relayMessagefunction lacked sufficient validation of the_targetaddress. It allowed the execution of arbitrary calls to any address, including the token contracts holding the bridge's assets. - The Exploit: An attacker could craft a malicious cross-chain message targeting the MNT or ETH token contract on the destination chain. The message payload would encode a call to
approve(attacker, amount). Since theCrossDomainMessengerexecutes this call (making it themsg.sender), and it holds the locked funds, the token contract would grant the attacker approval to spend the bridge's assets. The attacker could then drain the funds usingtransferFrom.
- A critical vulnerability was identified in Mantle's
- References:
2024-04-15 - 4
- Date: 2024-04-15
- Project: SumerMoney
- Value Lost: ~$350,000
- Chain: Base
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.1.1: Standard Reentrancy - Secondary Classification:
BWC 5.2.1: Price Manipulation
- Broader Classification:
- Description:
- The SumerMoney protocol (a Compound fork) was exploited due to a deviation from the standard Checks-Effects-Interactions pattern in its loan repayment logic.
- The Flaw: The
repayBorrowfunction refunded excess ETH to the caller before updating the globaltotalBorrowsstate variable. - The Exploit: An attacker repaid a loan with a 1 wei surplus. When the contract transferred this 1 wei refund, it triggered the attacker's fallback function. At this precise moment, the protocol held the repaid cash, but the
totalBorrowsfigure had not yet been decreased. This temporary state inconsistency caused the exchange rate (calculated as(Cash + Borrows - Reserves) / Supply) to spike artificially. Inside the reentrancy hook, the attacker redeemed their collateral at this inflated rate, receiving significantly more underlying assets than they were entitled to.
- References:
2024-04-16 - 3
- Date: 2024-04-16 (Audit Disclosure)
- Project: Mantle Network (op-geth)
- Value Lost: $0 (Critical Vulnerability Patched)
- Chain: Mantle
- BWC:
- Broader Classification:
BWC 1: Ecosystem & Off-Chain Risks - Primary Classification:
BWC 1.4.5: Client Consensus Bug - Secondary Classification:
BWC 6.1: Integer Overflow & Underflow
- Broader Classification:
- Description:
- A critical vulnerability was discovered in Mantle's execution client (
op-geth) during an audit. The flaw was located in the state transition logic that handles L1-to-L2 ETH deposits. - The Flaw: When processing a deposit, the Go code calculated the balance change using
BigIntsubtraction. If the "from" address had insufficient funds, the result would be a negative number. The critical failure occurred in thecommon.BigToHashfunction, which blindly converted this negativeBigIntinto a positive 32-byte hash (essentially underflowing/wrapping to a massive positive value) when writing to the state trie. - Impact: This would have allowed an attacker to initiate a transfer they couldn't afford, resulting in their balance being set to a near-infinite amount instead of reverting, effectively enabling infinite ETH minting on L2.
- A critical vulnerability was discovered in Mantle's execution client (
- References:
2024-04-26 - 2
- Date: 2024-04-26 (Audit Report Date)
- Project: Taiko (TimelockTokenPool)
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum / Taiko (Layer 2)
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.3.2: Incomplete Signature Schemes
- Broader Classification:
- Description:
- A critical vulnerability was identified in the
TimelockTokenPoolcontract used for Taiko grants. The contract allowed recipients to withdraw tokens using a signature authorization. - The Flaw: The signature validation logic relied on a weak digest:
keccak256(abi.encodePacked("Withdraw unlocked Taiko token to: ", _to)). This digest failed to include critical replay protection fields: a nonce (to prevent reusing the same signature on the same contract), the verifying contract address (to prevent reusing the signature on different pools), and the chain ID (to prevent cross-chain replays). - The Exploit: An attacker (or a malicious recipient) could capture a valid signature used for one withdrawal and replay it multiple times to drain the pool of all unlocked tokens allocated to that grant, or potentially replay it on other chains or contract instances.
- A critical vulnerability was identified in the
- References:
2024-04-26 - 1
- Date: 2024-04-26
- Project: Renzo Protocol
- Value Lost: $0 (Audit Finding)
- Chain: N/A (Audit Finding)
- BWC:
- Broader Classification: BWC 8: Denial of Service (DoS) Vulnerabilities
- Primary Classification: BWC 8.1: DoS via External Calls
- Description:
- The vulnerability was caused by using a low-level
payable.transfer()call, which forwards a fixed 2300 gas stipend, to send funds to a user withdrawing from the protocol. - The auditor identified that if the user's withdrawal address was a multi-sig wallet (e.g., Gnosis Safe), its fallback
receive()function would fail due to the insufficient gas stipend. - This issue was critical because the withdrawal mechanism required the final claimant to be the exact same address that initiated the withdrawal.
- This created a permanent DoS scenario: the Gnosis Safe could not receive the funds due to the low gas, but it was the only entity authorized to complete the withdrawal, leading to a permanent loss of funds for that user.
- The vulnerability was caused by using a low-level
- References:
2024-03-03 - 2
- Date: 2024-03-03 (Blog Series Publication)
- Project: Stargate / Drips Network
- Value Lost: $0 (Critical Vulnerability Disclosure)
- Chain: Omnichain (LayerZero Integrations)
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.8: DoS in Cross-Chain Messaging Protocols - Secondary Classification:
BWC 8.7: DoS via Return Data Bomb(Resource Exhaustion)
- Broader Classification:
- Description:
- Vulnerabilities were identified in how Stargate and Drips Network integrated LayerZero, leading to permanent channel blocking.
- Stargate DoS: Stargate used a
try-catchblock to handle failed payload deliveries. Researchers found two ways to bypass this safety mechanism:- EOA Target: Sending a payload to an Externally Owned Account (EOA) or a non-contract address could force the
try-catchto revert unexpectedly without entering the catch block, blocking the nonce. - Storage Exhaustion: Sending an extremely large payload that consumes all gas when the
catchblock attempts to store it for retry. This causes the catch block itself to revert, preventing the system from clearing the nonce.
- EOA Target: Sending a payload to an Externally Owned Account (EOA) or a non-contract address could force the
- Drips Network DoS: The protocol lacked a recovery mechanism for messages that indefinitely reverted at the bridge level on the destination chain. An attacker could send a message designed to always revert, permanently blocking the channel and preventing any future updates or message delivery.
- References:
2024-03-03 - 5
- Date: 2024-03-03 (Blog Series Publication)
- Project: LayerZero V1
- Value Lost: $0 (Critical Vulnerability Disclosure)
- Chain: Omnichain (LayerZero)
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.8: DoS in Cross-Chain Messaging Protocols - Secondary Classification:
BWC 8.11: DoS via Front-Running (Griefing)
- Broader Classification:
- Description:
- Security researchers at Trust Security disclosed multiple Denial of Service vectors in LayerZero V1.
- Nonce Overlap DoS: Messages were ordered by a nonce derived from
srcChain,srcAddress, anddstChain, but notably excluded thedstAddress. An attacker could configure a malicious application to send a message using the same nonce sequence as a legitimate application on the same path. By sending a "spoofed" message that fails or hangs, the attacker could block the delivery of the legitimate application's message with the same nonce, freezing the channel. - ONFT Gas DoS: In the ONFT (Omnichain NFT) implementation, the destination execution calls
onERC721Received. An attacker could bridge an NFT to a malicious contract on the destination chain that consumes all available gas in this callback. This would cause the delivery transaction to revert. Because LayerZero V1 enforced strict ordering, this failed message would block all subsequent messages on that path.
- References:
2024-03-21 - 4
- Date: 2024-03-21
- Project: Super Sushi Samurai
- Value Lost: ~$4,600,000
- Chain: Blast
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.4: Self Transfers and Transaction Timing Attacks - Secondary Classification:
BWC 3.2.5: Broken State Adjustment
- Broader Classification:
- Description:
- The Super Sushi Samurai (SSS) token was exploited due to a critical logic error in its custom ERC-20 transfer implementation regarding self-transfers.
- The Flaw: The
_updatefunction handled balance updates by first subtracting the amount from the sender (_balances[from] -= amount) and then adding it to the recipient (_balances[to] += amount). However, the implementation incorrectly calculated the new recipient balance before updating the sender's balance in storage. - The Exploit: When an attacker transferred tokens to themselves (
from == to), the contract would:- Calculate
toBalance(current balance + amount). - Update
_balances[from](current balance - amount). - Update
_balances[to]with the previously calculatedtoBalance. Sincefromandtoare the same storage slot, step 3 overwrote the deduction from step 2, resulting in the user's balance simply increasing by the transfer amount without the corresponding decrement, effectively doubling their balance with each self-transfer.
- Calculate
- References:
2024-03-05 - 3
- Date: 2024-03-05
- Project: WOOFI
- Value Lost: ~$8,750,000
- Chain: Arbitrum
- BWC:
- Broader Classification:
BWC 5: Economic & Game-Theoretic Vulnerabilities - Primary Classification:
BWC 5.2.1: Price Manipulation - Secondary Classification:
BWC 4.2.1: Insufficient Oracle Validation
- Broader Classification:
- Description:
- The WOOFI decentralized exchange was exploited due to a vulnerability in its Synthetic Proactive Market Making (sPMM) algorithm.
- The Flaw: The sPMM pricing mechanism, which adjusted prices based on on-chain trade volume to simulate an order book, was not adequately time-weighted or capped. It allowed a single block of transactions to drastically alter the asset's price.
- The Exploit: An attacker utilized flashloans to borrow large amounts of WOO and other assets. They executed a sequence of large swaps in a low-liquidity WOO market on Arbitrum, manipulating the sPMM to value WOO at an incredibly low price ($0.00000009).
- Secondary Failure: WOOFI had a safeguard designed to fall back to a Chainlink oracle if the price deviated too far. However, this fallback was not correctly configured for the WOO token on Arbitrum. Consequently, the system accepted the manipulated price, allowing the attacker to swap back and drain the pool's WOO reserves for pennies.
- References:
2024-03-28 - 2
- Date: 2024-03-28
- Project: Ondo Finance
- Value Lost: $0 (Audit Finding)
- Chain: N/A (Audit Finding)
- BWC:
- Broader Classification: BWC 5: Economic & Game-Theoretic Vulnerabilities
- Primary Classification: BWC 5.2.3: Hardcoded or Assumed Asset Price
- Description:
- The protocol allowed users to deposit USDC to mint the native OUSG token. The amount of OUSG minted was based on a price from an OUSG/USD oracle.
- The vulnerability was a flawed assumption in the minting calculation, which implicitly treated 1 USDC as being exactly equal to 1 USD.
- The code used the raw
usdcAmountInas the basis for the USD value of the deposit, without consulting a USDC/USD oracle. - During a de-peg event where USDC's market price is less than $1, an attacker could acquire USDC at a discount and deposit it into the protocol. The protocol would then mint OUSG tokens as if the deposited USDC was worth its full $1 value, granting the attacker an arbitrage opportunity at the expense of the protocol.
- References:
- Vulnerable Contract Code:
function _getMintAmount( uint256 usdcAmountIn, uint256 price ) internal view returns (uint256 ousgAmountOut) { uint256 amountE36 = usdcAmountIn * 1e18; ousgAmountOut = amountE36 / price; } - C423n4 Finding
- Vulnerable Contract Code:
2024-03-28 - 1
- Date: 2024-03-28
- Project: Prisma Finance
- Value Lost: ~$12,000,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.3.1: Missing Validation in Callbacks - Secondary Classification:
BWC 4.1.1: Insufficient Input Validation
- Broader Classification:
- Description: The
MigrateTroveZapcontract was exploited due to a critical validation failure in itsonFlashLoancallback function. This function was intended to be called only by the lending protocol as part of a legitimate flashloan-initiated migration process. However, the function failed to verify the context of the call or the input data source. This allowed an attacker to invokeonFlashLoandirectly with maliciously crafted data, instructing the contract to close other users' "Troves" (collateralized debt positions) and move their collateral. The attacker then manipulated the resulting position to withdraw the excess collateral for themselves. - References:
2024-02-05 - 1
- Date: 2024-02-05
- Project: Wrapped XETA (WXETA)
- Value Lost: ~$25,000 (Liquidity Pool Drained)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.1: Improper Initialization - Secondary Classification:
BWC 2.1.1: Missing Access Control
- Broader Classification:
- Description:
- The Wrapped XETA (WXETA) contract was exploited due to a critical re-initialization vulnerability.
- The Flaw: The contract's
initializefunction failed to properly set theinitializedstate variable (or check it correctly), leaving the contract open to being initialized again. - The Exploit: An attacker called the public
initializefunction on the already-deployed contract. This allowed them to overwrite the contract's owner/admin role with their own address. Once they gained admin privileges, they granted themselves minting permissions, minted a massive supply of WXETA tokens, and dumped them into the USDT/WXETA Uniswap pool to drain its liquidity.
- References:
2024-01-22 - 4
- Date: 2024-01-22 (Audit Disclosure)
- Project: Restake Finance
- Value Lost: $0 (Critical Audit Finding)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 3: Smart Contract Logic & State Manipulation - Primary Classification:
BWC 3.2.5: Broken State Adjustment - Secondary Classification:
BWC 7.2: Unsafe Storage & Memory Handling
- Broader Classification:
- Description:
- A critical logic error was identified in Restake Finance's withdrawal mechanism during an audit.
- The Flaw: The protocol processed withdrawals by sending the underlying assets to the user, deleting the
WithdrawalRequeststruct from storage, and then attempting to burn the corresponding shares. - The Exploit: Because the request object was deleted before the burn function was called, the subsequent read of
request.sharesaccessed a zeroed-out storage slot. Consequently, the function burned0shares instead of the correct amount. - The Impact: While users received their funds, the corresponding shares were never destroyed. This would lead to a permanent imbalance between the total share supply and the underlying assets, effectively diluting the protocol's exchange rate and breaking the accounting logic.
- References:
2024-01-16 - 3
- Date: 2024-01-16
- Project: Socket (Bungee Bridge)
- Value Lost: ~$3,300,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification:
BWC 2: Access Control Vulnerabilities - Primary Classification:
BWC 2.2.4: Composable Arbitrary Calls - Secondary Classification:
BWC 2.2.1: Unsafe Token Approvals
- Broader Classification:
- Description:
- The Socket (Bungee) bridge was exploited due to an arbitrary external call vulnerability in a newly deployed route handler.
- The Flaw: The contract's
performActionfunction processed user-suppliedswapExtraDatawithout validating the target or the calldata. - The Exploit: An attacker exploited this by passing the WETH contract address as the target and encoding a
transferFromcall in theswapExtraData. Because users had previously granted infinite WETH approvals to the Socket Gateway contract, the contract executed the malicioustransferFromcall as a "confused deputy," draining funds from user wallets directly to the attacker.
- References:
2024-01-12 - 2
- Date: 2024-01-12
- Project: Beanstalk (Immunefi Disclosure)
- Value Lost: $0 (Critical Vulnerability Patched)
- Chain: Ethereum
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.1.1: Insufficient Input Validation - Secondary Classification:
BWC 4.2.1: Insufficient Oracle Validation
- Broader Classification:
- Description: A critical vulnerability was discovered in Beanstalk's "Well" integration (liquidity pools). The protocol failed to validate the
Welladdress provided by a user during liquidity removal. Theconvertlogic trusted the input address to calculate the amount of BEAN tokens to return to the user. Because there was no whitelist or check to ensure the address was a legitimate Beanstalk Well, an attacker could have deployed a malicious contract that acted as a fake Well. This fake contract could report that the attacker was entitled to the entire BEAN balance of the Beanstalk contract, effectively allowing them to drain the silo without holding significant liquidity. - References:
2024-01-31 - 1
- Date: 2024-01-31
- Project: Abracadabra
- Value Lost: $6,500,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification: BWC 6: Arithmetic & Numeric Vulnerabilities
- Primary Classification: BWC 6.2: Precision Loss & Rounding Errors
- Secondary Classification: BWC 5.2.2: First Deposit / Inflation Attack
- Description:
- The exploit's root cause was a rounding issue in the CauldronV4 contract's borrow function. An attacker manipulated their share of the total debt by repeatedly borrowing and repaying small amounts of MIM, taking advantage of a rounding error.
- This attack was amplified by an ERC-4626 style inflation attack, where the attacker donated MIM to the BentoBox to manipulate the share price after repaying the debt of all other users.
- By repeatedly borrowing and repaying, the attacker exponentially increased their share of the debt (
part) while keeping the total borrowed assets low. This incorrect debt calculation allowed the attacker to borrow a large amount of MIM with very little collateral, draining the liquidity from theyvCrv3CryptoandmagicAPEcauldrons.
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2023 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2023-06-22 - 1
- Date: 2023-06-22 (Disclosure Date)
- Project: General EIP-2612 Implementations
- Value Lost: $0 (Vulnerability Disclosure)
- Chain: EVM
- BWC:
- Broader Classification:
BWC 8: Denial of Service (DoS) Vulnerabilities - Primary Classification:
BWC 8.11: DoS via Front-Running (Griefing) - Secondary Classification:
BWC 5.1.1: Front-Running
- Broader Classification:
- Description:
- Security researchers at Trust Security detailed a Denial of Service vector known as "Permit Griefing" affecting contracts integrating EIP-2612.
- The Flaw: Many contracts implement a "multicall" or "permit-then-execute" flow where
permit()is called to set token allowances before executing a trade or deposit. The contracts typically expect thepermit()call to succeed and will revert the entire transaction if it fails. - The Exploit: Because the permit signature is visible in the mempool, an attacker can front-run the user's transaction and submit the
permit()call themselves. The attacker's transaction succeeds, consuming the user's nonce and granting the approval. However, when the user's transaction subsequently attempts to callpermit()with the same (now used) nonce, it reverts. Although the approval exists, the user's intent (the trade or deposit) is blocked.
- References:
2023-12-06 - 1
- Date: 2023-12-06
- Project: TIME Contract ERC2771 Exploit
- Value Lost: $212,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification: BWC 4: Input & Data Validation Vulnerabilities
- Primary Classification: BWC 4.4.1: ERC-2771 + Multicall
- Description:
- The TIME contract was exploited due to a vulnerability in its
multicallfunction, which was set as a trusted forwarder for ERC-2771 meta-transactions. The issue stemmed from themulticallfunction not complying with the ERC-2771 standard for trusted forwarders. - The Flaw: A compliant trusted forwarder must append the original
msg.sender(20 bytes) to the end of the calldata it forwards. The TIME contract'smulticallfunction failed to do this. -
// Flawed Multicall implementation function aggregate(Call[] calldata calls) public payable returns (uint256 blockNumber, bytes[] memory returnData) { ... (success, returnData[i]) = call.target.call(call.callData); // Fails to append msg.sender ... } - The Mechanism: The
ERC2771Contextcontract, used for handling meta-transactions, retrieves the sender's address by reading the last 20 bytes of the calldata it receives from a trusted forwarder. -
// ERC2771Context logic to extract sender function _msgSender() internal view virtual override returns (address sender) { if (isTrustedForwarder(msg.sender) && msg.data.length >= 20) { assembly { sender := shr(96, calldataload(sub(calldatasize(), 20))) } } else { return super._msgSender(); } } - The Exploit: Because the flawed
multicalldidn't append the real sender, the last 20 bytes of the original calldata provided by the attacker were read by_msgSender. This allowed the attacker to craft a call where the last 20 bytes contained any address they wished to impersonate, such as the contract's owner, thereby bypassing access controls and draining funds. - The Fix: A secure
multicallimplementation appends the sender, ensuring the correct address is forwarded. -
// Secure Multicall3 implementation function aggregate(Call[] calldata calls) public payable returns (uint256 blockNumber, bytes[] memory returnData) { ... (success, returnData[i]) = call.target.call(abi.encodePacked(call.callData, msg.sender)); // Correctly appends msg.sender ... }
- The TIME contract was exploited due to a vulnerability in its
- References:
2023-09-25 - 1
- Date: 2023-09-25 (Disclosure Date)
- Project: Multiple Smart Accounts (ERC-1271 Implementations)
- Value Lost: $0 (Critical Vulnerability Disclosure)
- Chain: EVM Chains (Multi-chain)
- BWC:
- Broader Classification:
BWC 4: Input & Data Validation Vulnerabilities - Primary Classification:
BWC 4.3.2: Incomplete Signature Schemes - Secondary Classification:
BWC 4.3.1: Missing Signature Validation
- Broader Classification:
- Description:
- A widespread vulnerability was identified in the implementation of ERC-1271
isValidSignatureacross multiple smart account providers. - The Flaw: The standard implementation often only verified that the signature recovered to the correct
owneraddress. It failed to verify that the signature was intended specifically for the contract instance receiving it. - The Exploit: If a user deployed multiple smart accounts (e.g.,
Account AandAccount B) controlled by the same EOA key, a valid signature intended forAccount A(e.g., a Permit signature) could be replayed onAccount BbecauseAccount Bonly checked if the signer was the owner (which was true). This allowed attackers to replay authorizations across different accounts or chains owned by the same user. - Vulnerable Code Pattern:
function isValidSignature(bytes32 _hash, bytes calldata _signature) external view returns (bytes4) { // VULNERABLE: Only checks signer identity, not the destination scope if (recoverSigner(_hash, _signature) == owner) { return 0x1626ba7e; } else { return 0xffffffff; } }
- A widespread vulnerability was identified in the implementation of ERC-1271
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2020 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2020 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2020 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2020-03-12 - MakerDAO Black Thursday
- Date: 2020-03-12
- Project: MakerDAO
- Value Lost: $8,300,000
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification: BWC 5: Economic & Game-Theoretic Vulnerabilities, BWC 1: Ecosystem & Off-Chain Risks
- Primary Classification: BWC 5.4.1: Cascade Failure from Network Congestion, BWC 1.3.7: Flawed Off-Chain Infrastructure
- Description:
- On "Black Thursday," a massive ETH price drop caused extreme network congestion and gas price spikes on Ethereum.
- This led to a cascade of failures in the MakerDAO system:
- Oracle Lag: Price oracles failed to update in a timely manner due to the high gas fees.
- Mass Liquidations: When the oracles finally updated with a much lower price, a large number of collateralized debt positions (CDPs) were liquidated simultaneously.
- Keeper Failure: The reference keeper software, used by most auction bidders, was not designed to handle the extreme gas prices and failed to submit bids.
- Zero-Bid Auctions: The lack of competing bids allowed a few liquidators to win collateral auctions with bids of 0 DAI, extracting over $8.3 million worth of ETH for free.
- This incident was a systemic failure caused by the protocol's inability to handle extreme market volatility and network congestion, coupled with a critical failure in its off-chain keeper infrastructure.
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2017 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2017-11-06 - Parity Multi-Sig Library Self-Destruct
- Date: 2017-11-06
- Project: Parity
- Value Lost: $300,000,000 (approx. 513,774 ETH frozen)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification: BWC 3: Smart Contract Logic & State Manipulation
- Primary Classification: BWC 3.2.1: Improper Initialization
- Description:
- The Parity multi-signature wallets relied on a single shared library contract for their logic (acting as the implementation for many light proxies).
- This library contract was deployed but left uninitialized, meaning it had no owner.
- A user (
devops199) was able to call theinitWalletfunction on the library contract itself, effectively claiming ownership of the standard library. - The user then triggered the
kill()function (Tx: 0x47f7...f690), which executedselfdestruct. - The destruction of the library contract rendered all dependent multi-sig wallets non-functional, permanently freezing the funds held within them.
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
2016 EVM Contract Vulnerability Incidents Classification & Analysis.
This database uses the BWC to classify Contract Vulnerability Incidents. Note off-chain issues have been excluded they're the most prevalent and resulted in more values lost. Humans remains to be the weakest point human stupidity or ingenuity(depending on how you look at it) could be infinite. It's unfeasible to track it.
2016-06-17 - The DAO Hack
- Date: 2016-06-17
- Project: The DAO
- Value Lost: $60,000,000 (approx. 3.6M ETH)
- Chain: Ethereum Mainnet
- BWC:
- Broader Classification: BWC 3: Smart Contract Logic & State Manipulation
- Primary Classification: BWC 3.1.1: Standard Reentrancy
- Description:
- The DAO smart contract contained a critical reentrancy vulnerability in its
splitDAOfunction. - The contract logic performed an external call to send Ether to the user before updating the user's internal balance (or share count).
- The attacker deployed a malicious contract with a fallback function. When The DAO contract sent ETH to this malicious contract, the fallback function triggered, recursively calling the
splitDAOfunction again. - Since the state (balance) hadn't been updated yet, the subsequent calls were also successful, allowing the attacker to drain funds repeatedly in a single transaction stack.
- This event led to the controversial hard fork that created Ethereum (ETH) and Ethereum Classic (ETC).
- The DAO smart contract contained a critical reentrancy vulnerability in its
Vulnerable Code Pattern
// Simplified representation of the vulnerability
mapping(address => uint) public balances;
function withdraw() public {
uint amount = balances[msg.sender];
// Check
require(amount > 0);
// Interaction (Vulnerability: External call before state update)
(bool sent, ) = msg.sender.call{value: amount}("");
require(sent, "Failed to send Ether");
// Effect
balances[msg.sender] = 0;
}
- References:
It’s important to emphasize that the intent behind this content is not to criticize or blame the affected projects but to provide objective overviews that serve as educational material for the community to learn from and better protect projects in the future.
Services Agreement Template for a Smart Contract Audit
This Services Agreement ("Agreement") is entered into between [Client Name], hereinafter referred to as "Client," and [Auditor Name], hereinafter referred to as "Auditor," collectively referred to as the "Parties."
1. Scope of Work
The Auditor agrees to perform a security audit of the Client's smart contracts deployed on [blockchain network], specifically [list contract addresses or repository links]. The audit will assess the code for vulnerabilities, logic errors, and compliance with industry best practices.
2. Audit Process
- Initial Review: The Auditor will perform an initial assessment of the smart contract code and share preliminary findings.
- Client Feedback: The Client may address the findings and implement fixes based on the initial review.
- Final Review: The Auditor will review the updated code and prepare a final audit report.
- Report Delivery: The final report will detail vulnerabilities, recommendations, and an overall security assessment.
3. Timeline
The audit will begin on [start date] and is expected to conclude by [end date], with the final report delivered by [report delivery date]. The Auditor is available to work from the 1st to the 21st of each month, dedicating 12 hours per day, 7 days a week, for a total of 21 consecutive days.
4. Pricing and Payment Terms
4.1 Pricing Formula
The total fee for the audit is calculated based on the number of Solidity lines of code (SLOC), determined using the following method:
- Code Formatting:
The Solidity code must be formatted using forge fmt with the following settings:
export FOUNDRY_FMT_SINGLE_LINE_STATEMENT_BLOCKS="multi" export FOUNDRY_FMT_LINE_LENGTH=90 export FOUNDRY_FMT_TAB_WIDTH=4 export FOUNDRY_FMT_MULTILINE_FUNC_HEADER="params_first_multi" export FOUNDRY_FMT_BRACKET_SPACING=false export FOUNDRY_FMT_INT_TYPES="long" export FOUNDRY_FMT_QUOTE_STYLE="double" export FOUNDRY_FMT_NUMBER_UNDERSCORE="thousands" export FOUNDRY_FMT_HEX_UNDERSCORE="remove" export FOUNDRY_FMT_OVERRIDE_SPACING=false export FOUNDRY_FMT_WRAP_COMMENTS=false export FOUNDRY_FMT_CONTRACT_NEW_LINES=true export FOUNDRY_FMT_SORT_IMPORTS=true - Counting Lines of Code: After formatting, the SLOC will be calculated using cloc, a GNU utility, based on its output for Solidity files.
- The total fee is determined by the formula:
Where:
-
( a ) = SLOC, as calculated by cloc after formatting with forge fmt using the settings above.
-
Testing factor = 2 (if the Client provides tests) or 3 (if the Auditor must write tests for Proof of Concept (POC)).
-
Audit Time: The adjusted SLOC (after applying the testing factor) is divided by 200 (assuming the Auditor audits 200 SLOC per hour).
-
Report Compilation: An additional 12 hours is added for compiling the audit report and quality-of-life (QOL) documentation.
-
Hourly Rate: The total hours are multiplied by the Auditor’s rate of {200 USD} per hour.
4.2 Deposit
The Client shall pay a 30% non-refundable deposit of the estimated total fee upon signing this Agreement. The estimate will be based on an initial SLOC count provided by the Client.
4.3 Final Payment
The final payment will be adjusted based on the actual SLOC count at the time of the audit and is due upon delivery of the final audit report.
4.4 Payment Method
Payments shall be made in [cryptocurrency, e.g., ETH, USDC] to the Auditor’s wallet address [wallet address].
4.5 Late Payments
Late payments will incur interest at [rate] per [time period].
5. Responsibilities
Client Responsibilities:
- Provide the final commit of the smart contracts by [date].
- Indicate whether tests are provided or if the Auditor must write tests for POC.
- Be available for meetings and discussions as required.
- Implement recommended fixes from the audit findings.
Auditor Responsibilities:
- Perform the audit with professionalism and diligence.
- Deliver a comprehensive final report by the agreed delivery date.
- Maintain confidentiality of the Client’s information.
6. Changes and Unforeseen Circumstances
-
Scope Changes: Any changes to the scope must be agreed in writing and may adjust the timeline and fees. New functionality added during the fix audit may incur additional costs.
-
Auditor Unavailability: If the Auditor cannot perform the audit due to unforeseen circumstances, a qualified replacement will be provided, or the timeline will be adjusted.
-
Client Delays: If the Client is not ready by the start date, the Auditor may reschedule or charge additional fees.
-
SLOC Disputes: Any disagreements over the SLOC count will be resolved by re-running cloc on the code formatted with the specified forge fmt settings.
7. Intellectual Property
The Auditor retains ownership of any tools, methodologies, or concepts developed during the audit, unless otherwise agreed.
8. Liability Limitations
The Auditor is not liable for undetected vulnerabilities or exploits after the audit. The Client understands that the audit is a point-in-time evaluation and does not ensure absolute security.
9. Cancellation Policy
The Client may cancel with at least 7 days’ notice, forfeiting the deposit. Cancellations with less than 7 days’ notice will incur a fee of 50% of the estimated total fee. The Auditor may cancel if the Client fails to meet their obligations, with the deposit remaining non-refundable.
10. Dispute Resolution
Disputes arising from this Agreement will be resolved through [mediation, arbitration, or jurisdiction-specific legal process].
11. Compliance and Legal Framework
The Client confirms that all funds used for payment are from legitimate sources and comply with anti-money laundering (AML) regulations. The Auditor may require the Client to complete know-your-business (KYB) procedures before starting the audit. Both Parties agree to adhere to applicable laws and regulations.
12. Miscellaneous
Confidentiality: Both Parties will protect sensitive information shared during the engagement. Report Publication: The Auditor may publish the audit report after 30 days from delivery, unless the Client objects in writing. Governing Law: This Agreement is governed by the laws of [jurisdiction].
13. Signatures
By signing below, both Parties confirm they have read, understood, and agree to be bound by this Agreement.
[Client Signature] [Date] [Auditor Signature] [Date]